¶ PVYdevices | User Guide
For a quickstart, please consult our QuickStart Guide.
¶ PVYdevices Desktop App
On all Operating Systems PVYdevices currently supports (macOS, Linux, Windows, ChromeOS) you will find an Application called PVYdevices Desktop App. It’s being installed with the PVYdevices Agent and offers to the User of that Device:
- Transparency - He can see what SysAdmins can see
- Interactions - Policy Violations or Missconfigured Applications are being displayed to him, with Guides how to solve the issue or option to instantly raise a Support Ticket for help
- Scheduled Maintenance with Calendar Entry, so he knows when Updates are performed
¶ Where the PVYdevices Desktop App can be accessed?
- Depending which Operating System, the short cut access varies a bit:
- macOS - Menu Bar
- Windows - Tray Icon
- Linux - Dock or Tray Icon, on some in Menu Bar
- ChromeOS - Dock Icon
¶ PVYdesktop App has following Interactions for the End user
User can see his Device on PVYdevices with the same Informations as Sys Admins can see, just without any further interactions, in a read status. The Access to its own Device Overview Page is being granted with an tokenized URL. If user has additional an own Login to PVYdevices with the role “Observer” or higher, he can also see other devices and based on the given setting to that role, he can perform its own queries and more.
¶ PVYdevices Desktop App Menu Items
MyDevice
This Menu entry logs the user via Web Browser to PVYdevices tokenized URL to its own Device Page with all the Information about his Device, such as Metrics, Last Actions, Planned Actions, Software Inventory, CVE Vuln Overview his Device was affected to.
Transparency Report
This Menu Items leads to PVYwiki Transparency Declaration, so the user can see and learn, what PVYdevices sees and what not.
Policy Violations
If Device has a new Policy Violiation or Vulnabrity, its being displayed to user, with Instruction for Self Service or to open a PVYserviceDesk Ticket.
¶ Cyber Security doesn’t need espionage
¶ What personal information PVYdevices can see?
End users deserve to know what their employer can see on their laptops and the systems they manage for Application and OS Updates, and Cyber Security. For this reason, we created on the PVYdevice Desktop App 3 Menu Options in the Menu Bar (macOS, Linux) or in Systemtray (Windows, some Linux):
¶ My Device
It logs you to the PVYdevices Monitoring Services and you as a user see exactly the same, what your IT System Admin sees, and you also can perform a few queries and Status checks. Your Organisation System Admin has just more Option, to enable Policies, Queries, and Maintance your Updates or in Emergency, he can perform a script.
¶ Transparency
This Menu opens your Web Browser and lead to our Transparancy Documentation here. It further gives you advices, what you shall store on your device, and how to deal with real private informations in general.
¶ Ask for Support
PVYdevices can be linked and automated with PVYserviceDesk. But also the API for ZendDesk and Fresh is being provided. If User use the Menu Option to ask for Support, the System will create a Support Ticket on the counter part, with your User and Device Name. It can then be either called and screenshared over PVYmessenger or enabling true Remote Desktop with PVYremote to assist the User in its case.
¶ PVYdevices Agents
Based on OSquery, you can download as PVYdevices User within your PVYcentral Management Concole the Package Installers for PVYdevices for:
- macOS
- Chromium
- Linux Debian
- Linux RHEL
- Windows
- Docker
All Installers are being automatically signed with your own Domain you have assigned to your PVY@Cloud Services or PVY@Office Appliance, so they also pass macOS Gatekeeper or Windows Firewall Settings properly. Update mechanism included. Furthermore, you can change and manage in the Settings of PVYdevices, what the Agent shall perform on Queries, Intervalls and so one, and they will update with these settings within the next 10 seconds.
¶ PVYdevices Scripts
PVYdevices let your SysAdmins, if enababled, manage Incidents or correct critical parameters on an enrolled PVYdevice Host. Currently there are following Scripts supported:
- bin/sh
Powershell on Windows is being supported. All uploaded scripts will be executed as “root” and let SySAdmin execute a custom script to remediate an issue on your macOS, Windows, and Linux hosts.
The Script Functionality can be accessed under the Main Menu Item “Controls” and is only enabled by default in conjuntion with PVYdevices MDM Functionality.
¶ PVYdevices Default Query Library
PVYdevices included by Default all useful osqery available you may want to use within your Policies and Automatisations for Windows, Linux, macOS and ChromeOS.
On top of the roughly 300 Queries from OSqery itself, we include following additional Query Libraries:
- Palantir
- Fleet
- Kolide
You can always create and add our own custom queries, either for adhoc queries or for repeatingly or automated queries with automatisation workflows. It’s a comprehensive Stack which let you manage your enterprise fleet on devices in a professional manner.
¶ PVYdevices Default Policies Library
PVYdevices also included all nowadays default used Policies for securing your hosts enrolled with PVYdevices regardless if you manage just 5 Desktops/Notebooks or a few thousands. You can also, similar to built-in query builder, create adhoc new Policies, which indicates immediately, if an employee has installed unwanted software such as «Microsoft Teams».
¶ PVYdevices Automatisation
When you can combine the dedection of Application or Operating System Vulnerabilities, Policy Violation with Custom or System Queries with Automatisation, exactly the way you want it, you will end in a very comprehensive IT and Security Tool, which saves you valuable time by the same time you increase your Device and Server Security to a new level.
¶ PVYdevices User Interface & Navigation
¶ Header Navigation Bar
On top, when you logged in as an authorized IT Staff Member to manage and maintain Server, Dockers, Kubernetes or End User Devices, have 7 main navigation items:
- Dashboard (Logo)
- Hosts
- Controls
- Software
- Queries
- Policies
- Account/Settings
¶ Dashboard View
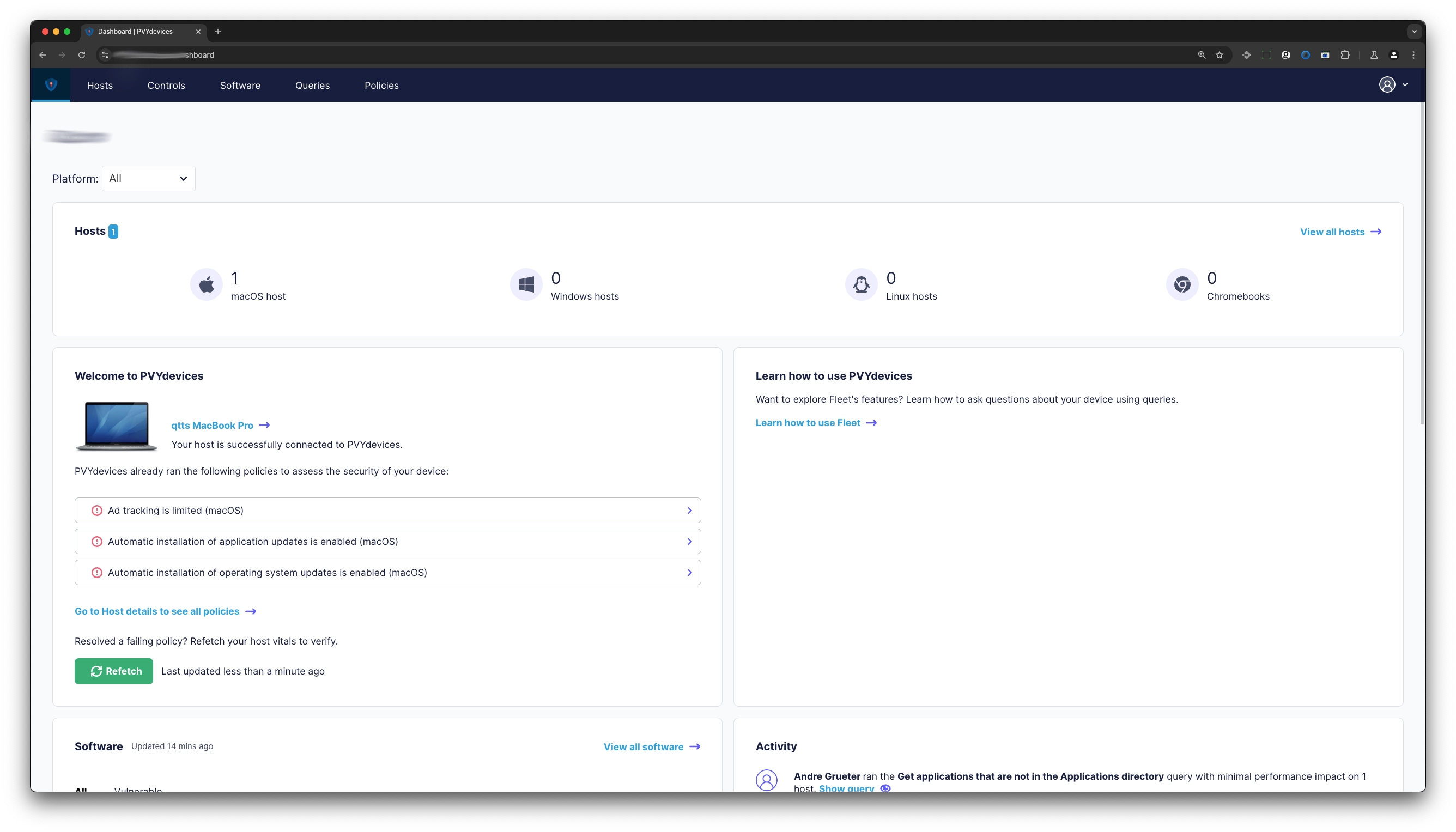
The Dashboard has 7 Containers which displays you as logged in user valueable information at first sight to give you a climpse overview about all Devices by OS, latest added devices and failed policies, Software Overview, newest on always on top, beside what is vulnerable.
The Acitivity Board gives you insights what other users performed recently on the system, and on the bottom you have your MDM Device Management related Solution Updates, Controls and Status for Quick Updates and Releases to perform, when Device is not set to automatic enrollement but manual.
¶ Hosts View
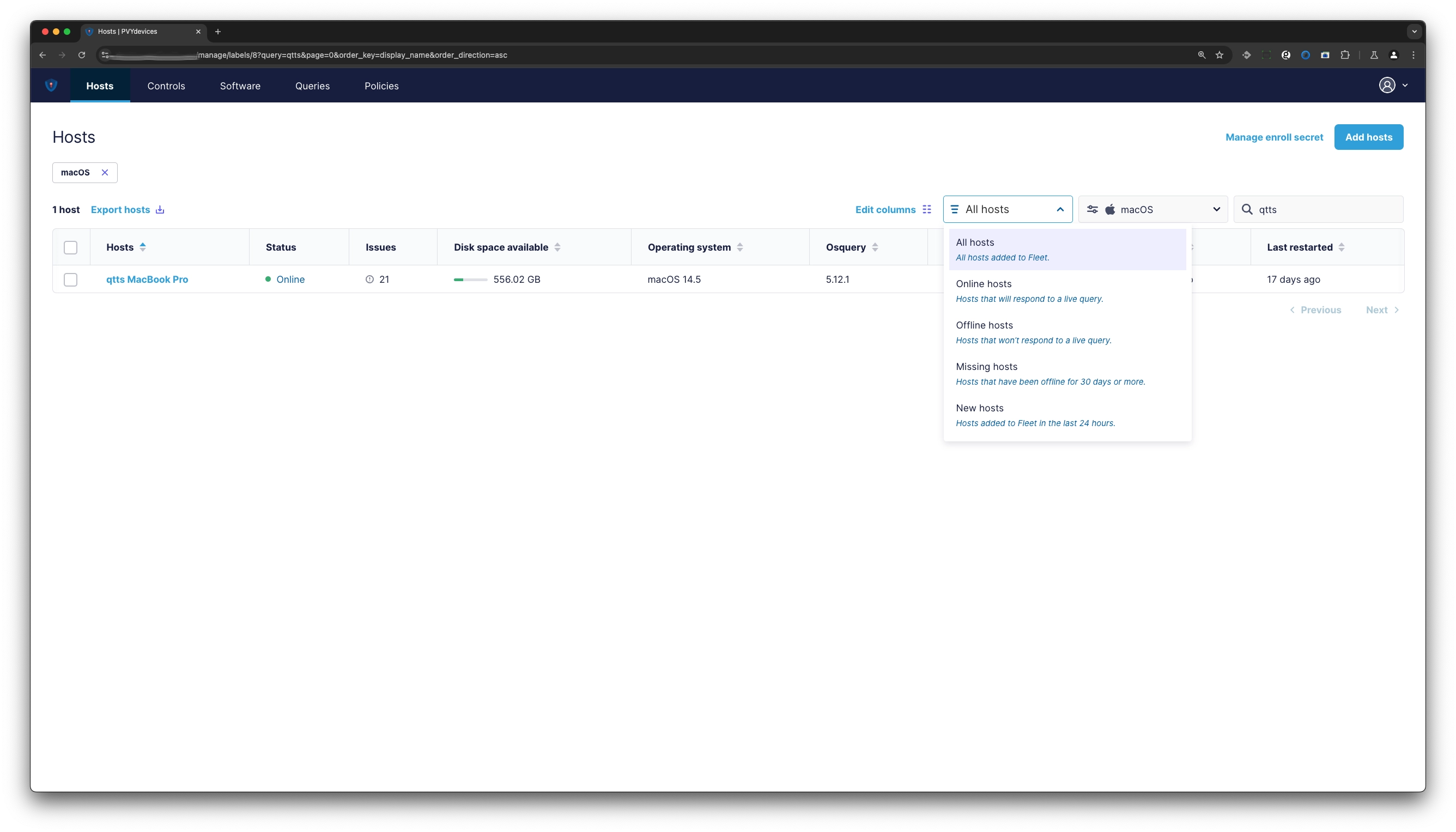
As on any list view, you can search, filter columns, filter based on Host Status Criteria or Operating System your target of interest.
¶ Host Details
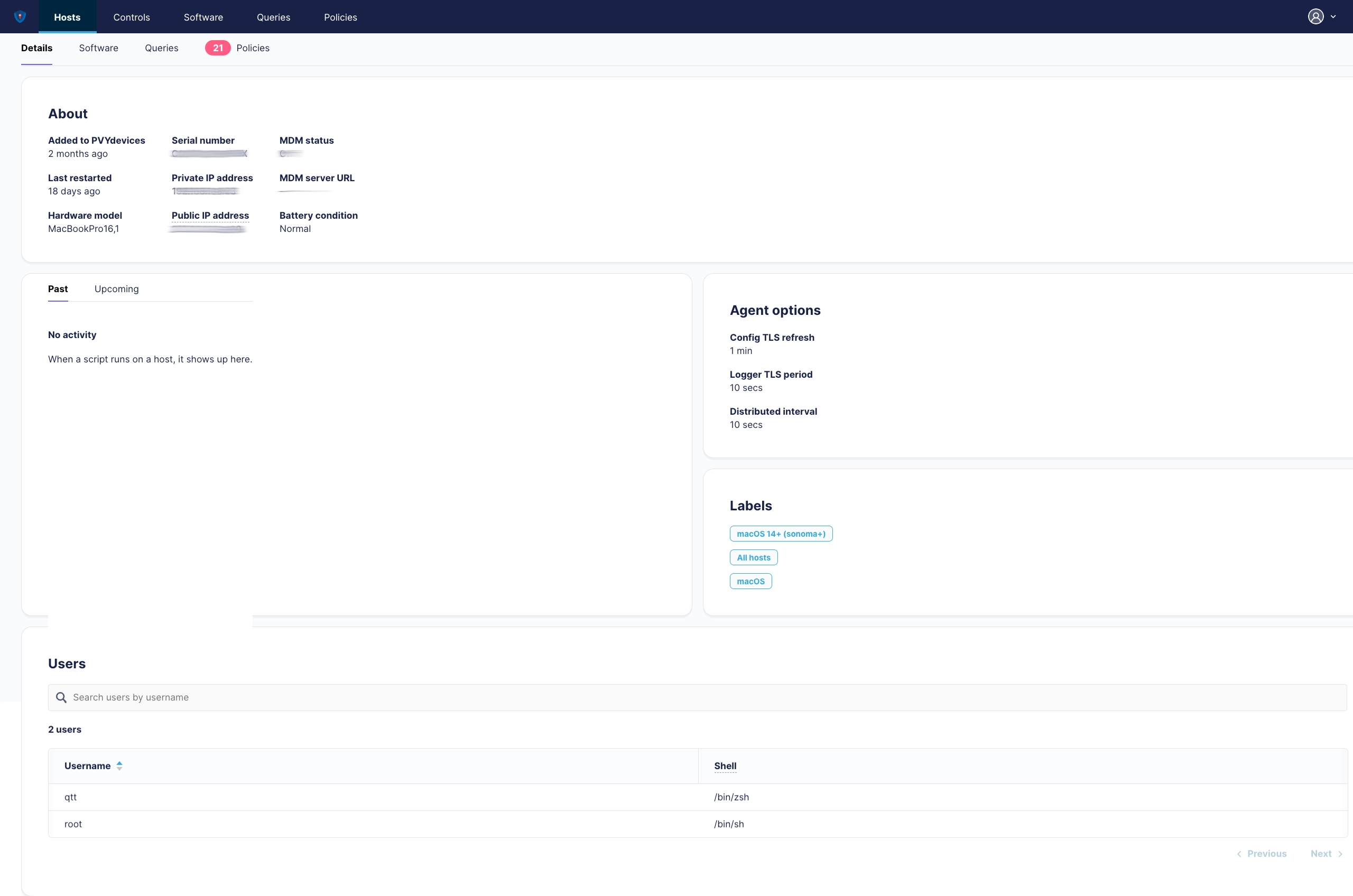
The Host Details shows up basic metrics, ips and the health of the device, including battery and PVYmdm Status. Further you can view and audit past and upcoming activities performed on the host, such as scripts uploaded manual to the host or in conjunction with Ansible, Chef or any other Orchestrator. As well MDM Activties.
¶ Host Software
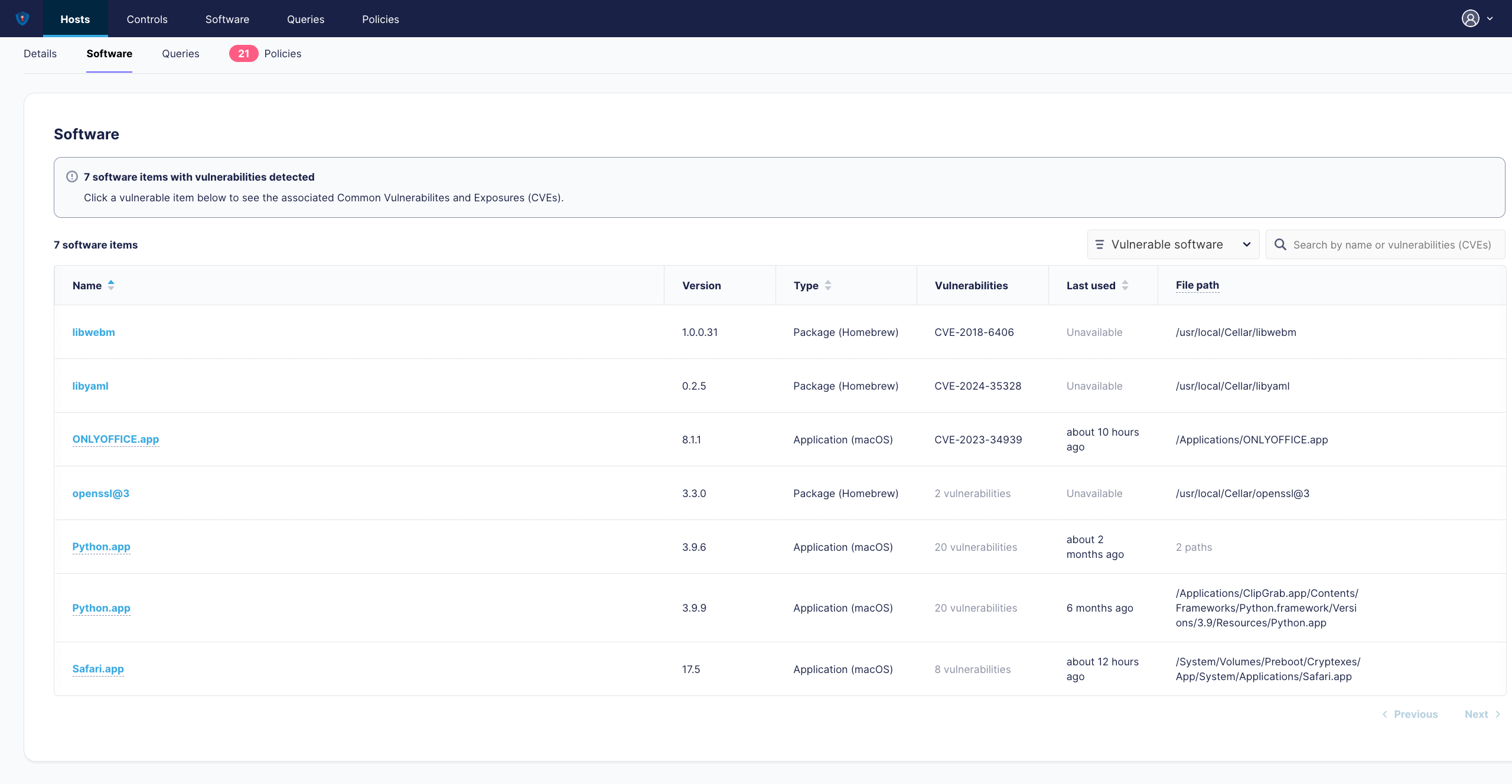
Lists browsable and searchable all installed Software of that specific hosts. Can be filtered for All Software, Vulnerable Software and sorted by Name, Version, Type, Vulnerabilities, Last used, File Path.
Like each Page, you can also trigger a refresh remote fetch to update current status, after some iterations has been performed, to check its reflected.
¶ Host Queries
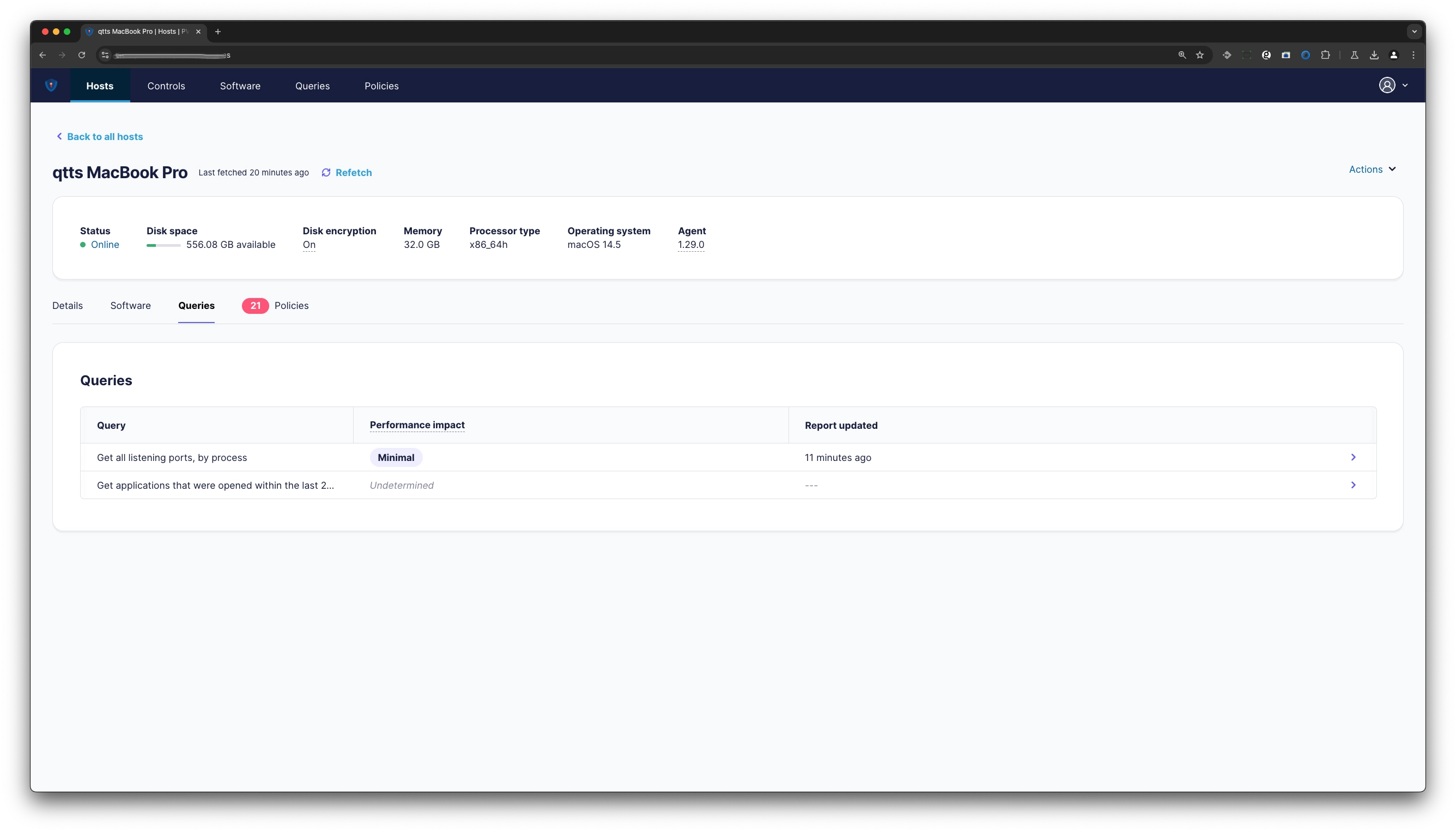
You can adhoc perform or create scheduled queries for a specific host, host group and you can obtain the queried results for that specific host on the Detail View. Optionally you can disable the log sendings, and define under automatisation any other log destination/application for more comprehensive analysis, such as PVYapplytics or CheckMK to name a view.
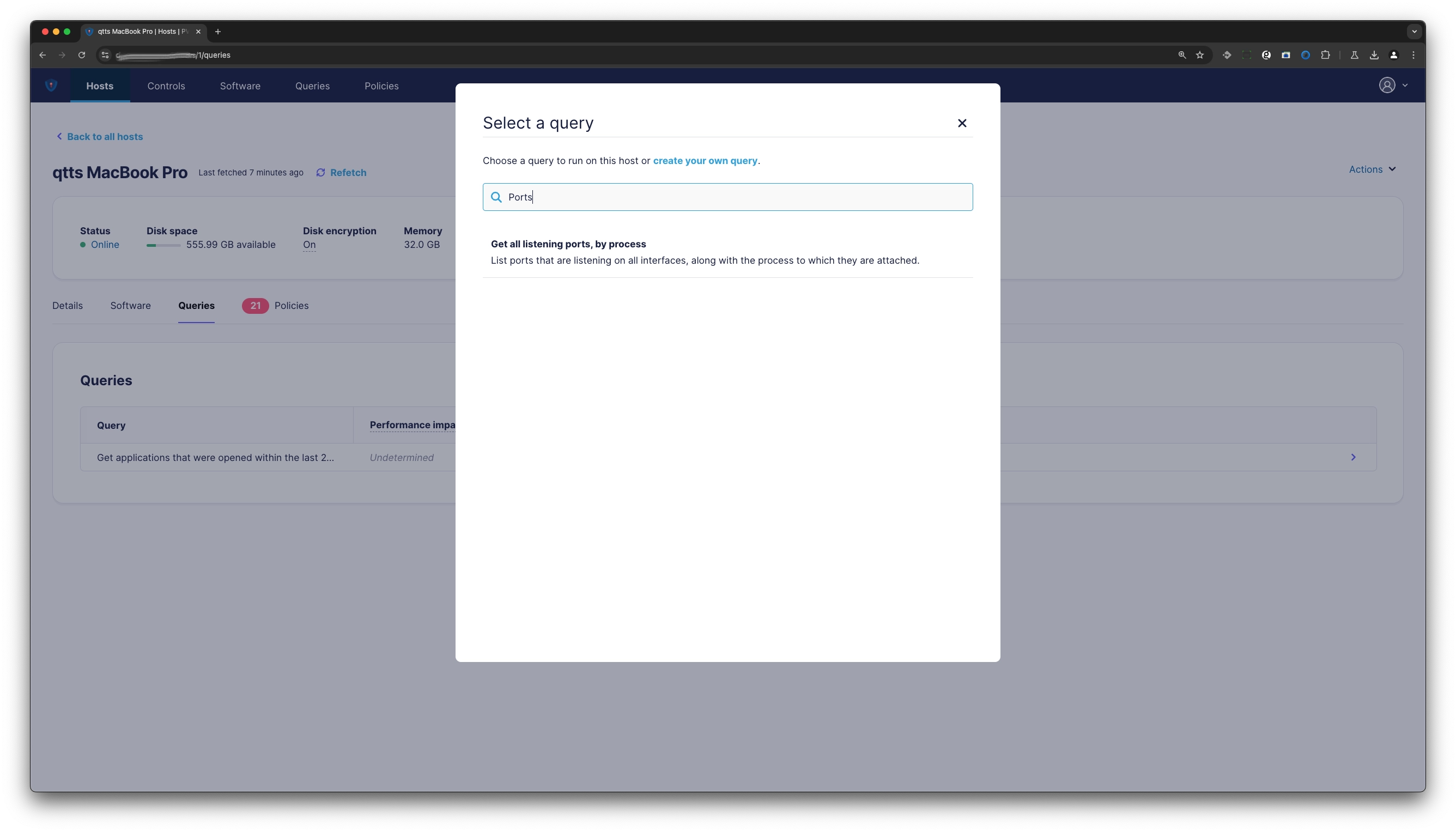
Its a very powerful tool, to enhance cybersecurity, compliances beyond policy checks. You can add anytime from over 300 pre-conifgured queries matching macOS, Linux, Windows, ChromeOS. We also included MITR Queries and some specific from Palantir.
You can also anytime create your own queries, either adhoc or save it as template, or scheduled query. Like on any result, you can export it as .CSV.
¶ Automate Queries
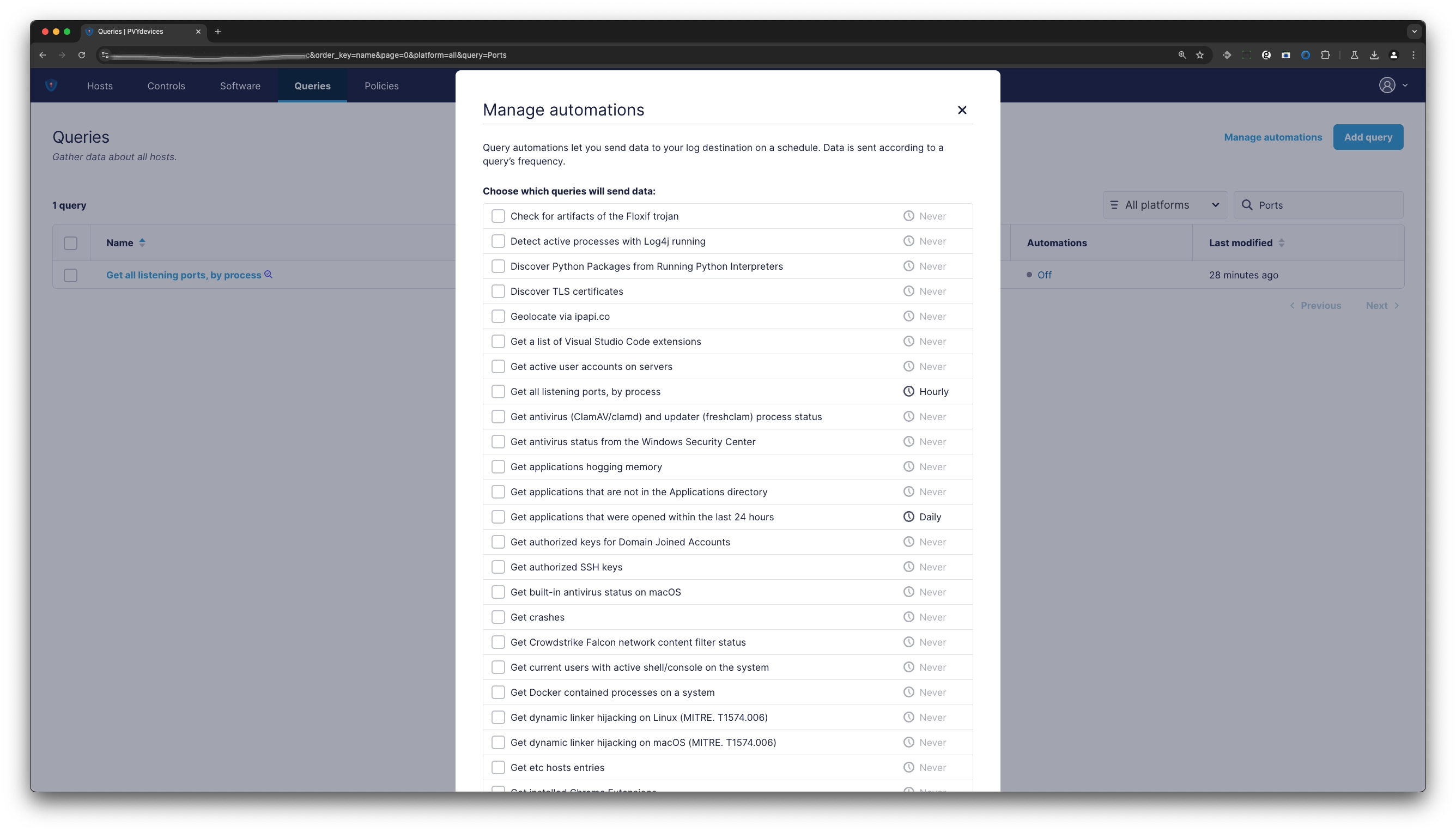
PVYdevices not only let you run queries, you can automate them based on certain schedules, such as:
- Evey Minute
- Every 15 Minutes
- Every 30 Minutes
- Every Hour and up to custom values for a daily or weekly routine
Further, you can match these queries to pre defined hosts, os group.
¶ Host Actions
You can always performe some action on any hosts connected with PVYdevices Agent and/or PVYmdm:
With PVYdevice Agent only:
- Start or Run a query
- Upload a Script ()
- Run a Script
- Delete Host from PVYdevices
Please note, if you delete a Host, you need to remove the Agent on the specific Device too. Therefore, you have to login to that device and run the Agent Removal Command in Terminal/Console. In near future, you can perform that remotely.
With PVYmdm connected:
- run OS Updates or schedule OS Updates
- run Application Updates or schedule Application Updates
- Correct Policies without User Interaction
- Manage your macOS or iOS Payloads, OS Updates and Applications, same for Windows and it’s Registry
Learn how to connect your PVYdevices to PVYmdm
¶ Host Policies
It’s a kind of magic. Transparent to its User if Device is allocated to a End User.
Let you steer policies with or without bonded PVYmdm.
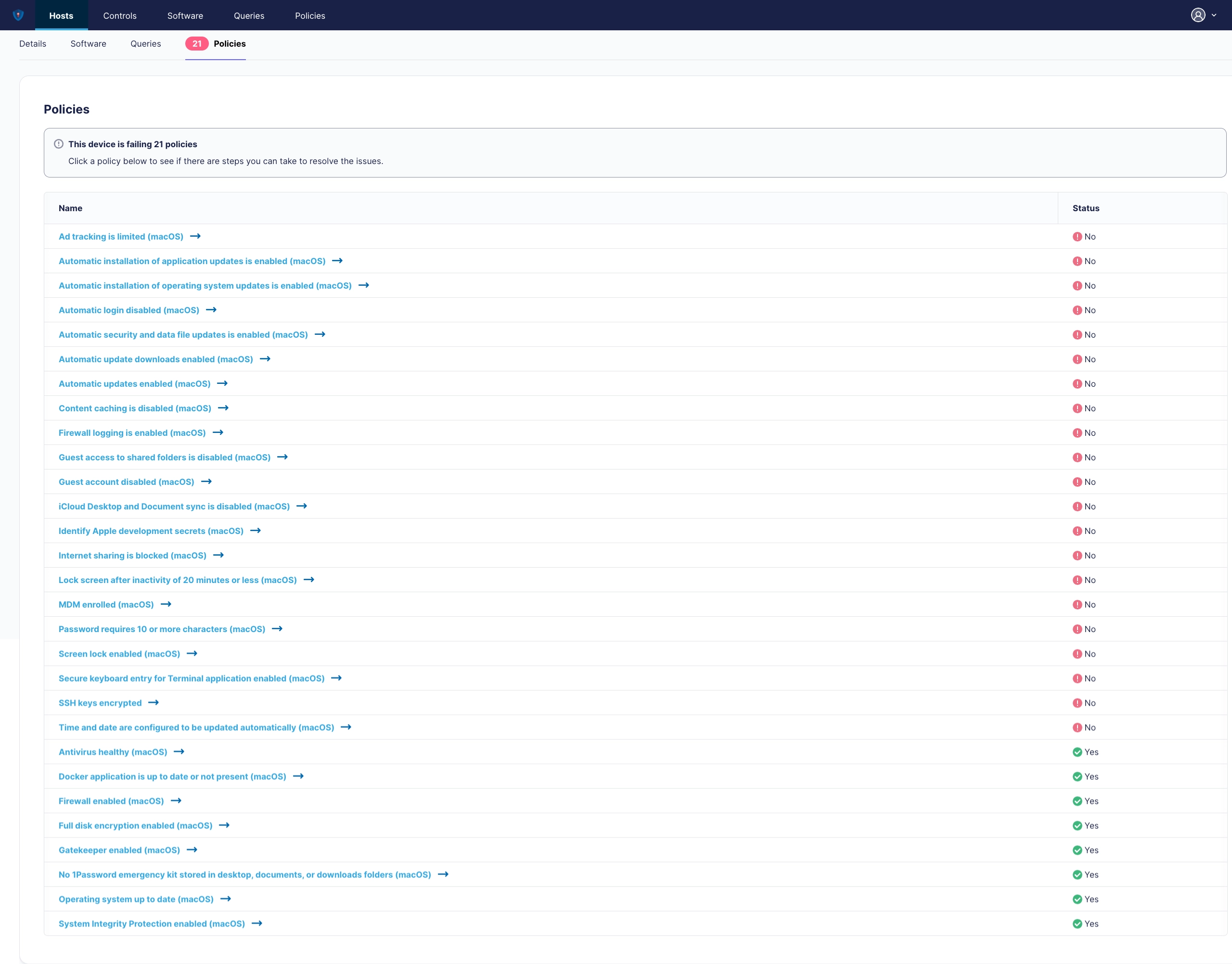
As you can see, this particular host is not yet enrolled to the PVYmdm, so Policies with checks related to an persistent MDM connection, will fail. Once enrolled, the IT Staff can automatically let failing policies correct, without the need for user interactions.
¶ Controls View
In the Menu Controls, you can see available OS Updates, OS Settings and Scripts, which have been uploaded to some of your hosts. This can be maintenance scripts, deployment scripts or in an emergency, of an infected host, you can use .sh, bash or PowerShell Script to maintain the host from inside out, since the scripts will be saved within the PVYdevice Agent, and are executible.
¶ Software View
This view gives you a complete overview over all installed software and libraries over all of your hosts, regardless if they are end user devices, iot devices, servers or docker containers. And it let you quickly filter them down not only by vulnerabilities, but also, with a click, you see which host are affected or running this application or software stack. 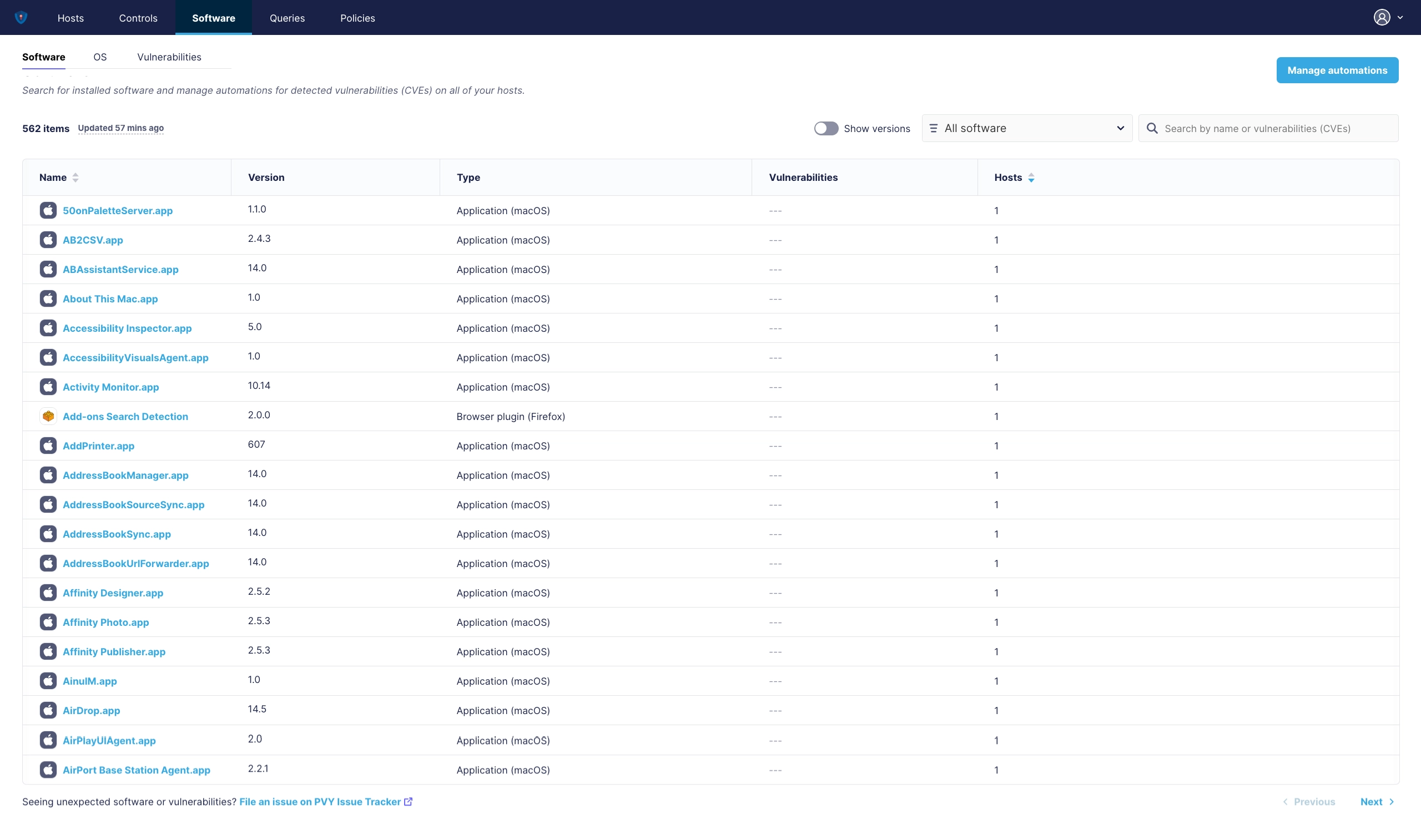
¶ It does that for:
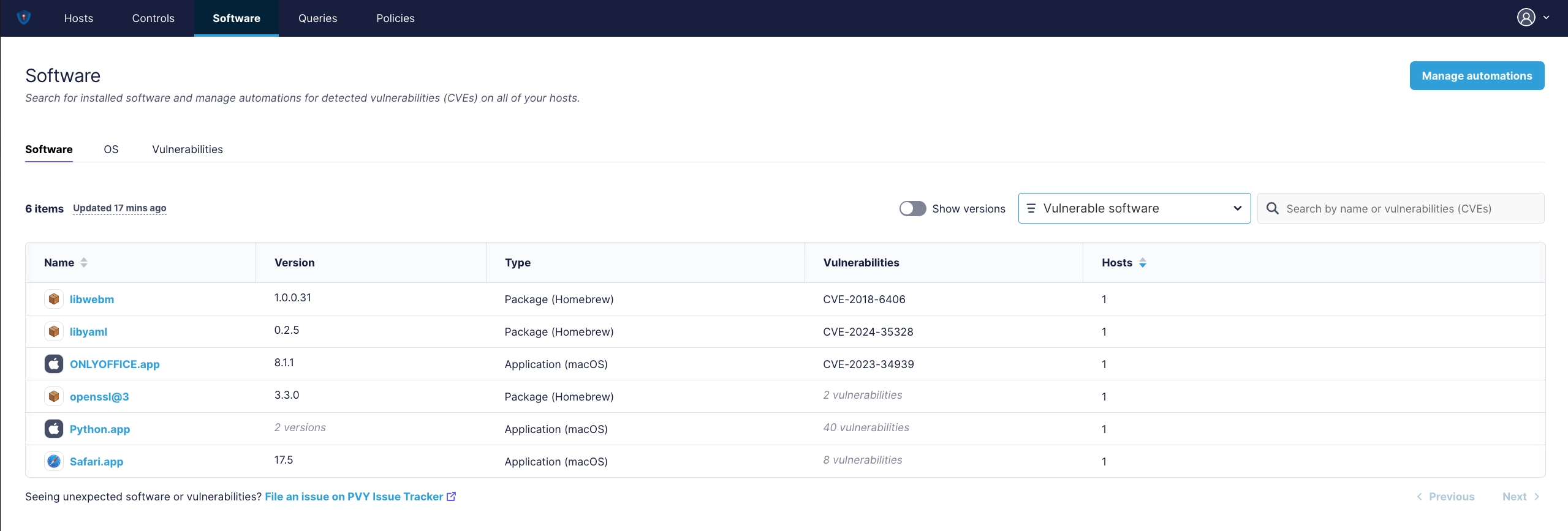
¶ Software Applications and related CVE’s
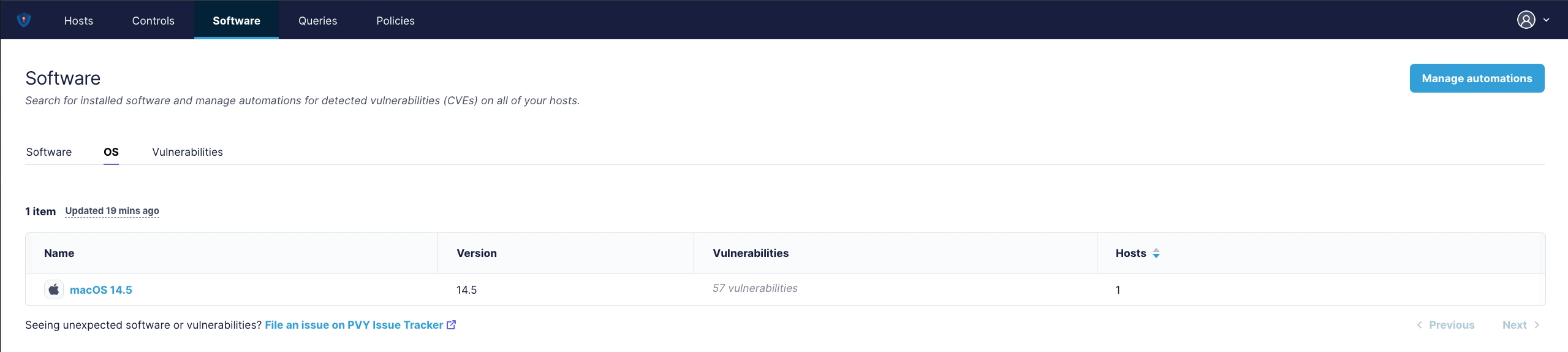
¶ Operating Systems and related CVE’s
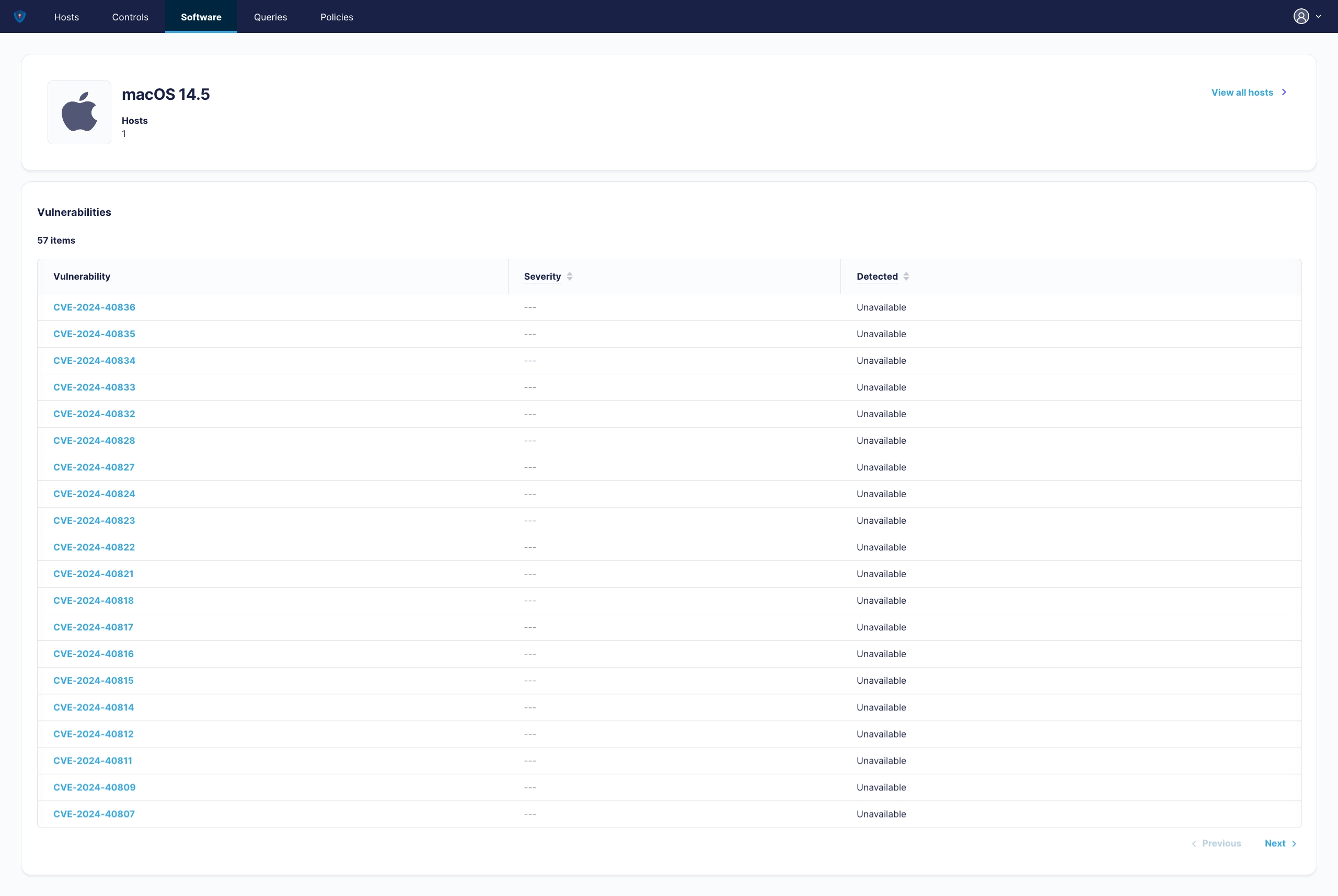
¶ Operating System Vulnerabilities Detail View
¶ All Vulnerabilities
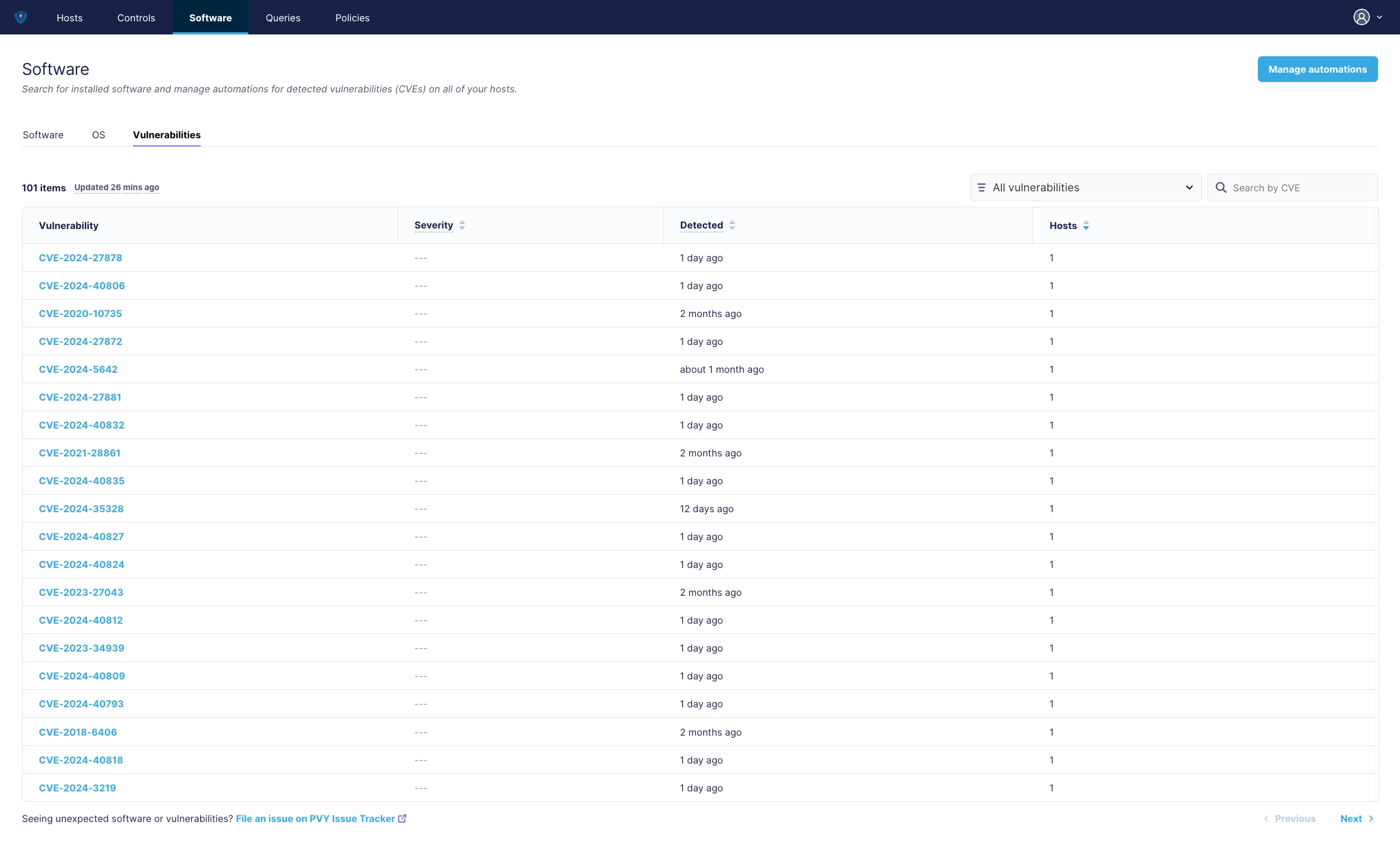
On the Tab for “Vulnerabilities” you have them filtered down to any kind of a Software Package which contains known CVE classified as vulnerable, and you can nail them down further into “exploitables”.
¶ How to manage Vulnerabilities
There are several approaches, based on Team and Infrastructre Size. You can also combine Policies to prevent for example, if an exploitable Software Package has been dedected, either to clean that from the system, which makes only sense on End User Devices, on Server you won’t do that, using automatisation to notify your NoC Team on PVYmesssenger with a collectively summeray, so they can check if all security measurements has been applied on Firewalls. Or, not always, but often already solve a few, deploy available hot-fixes or System/Application Updates.
There is also a managed Option available, both on PVY.swiss or PVYpartners.
¶ Queries View
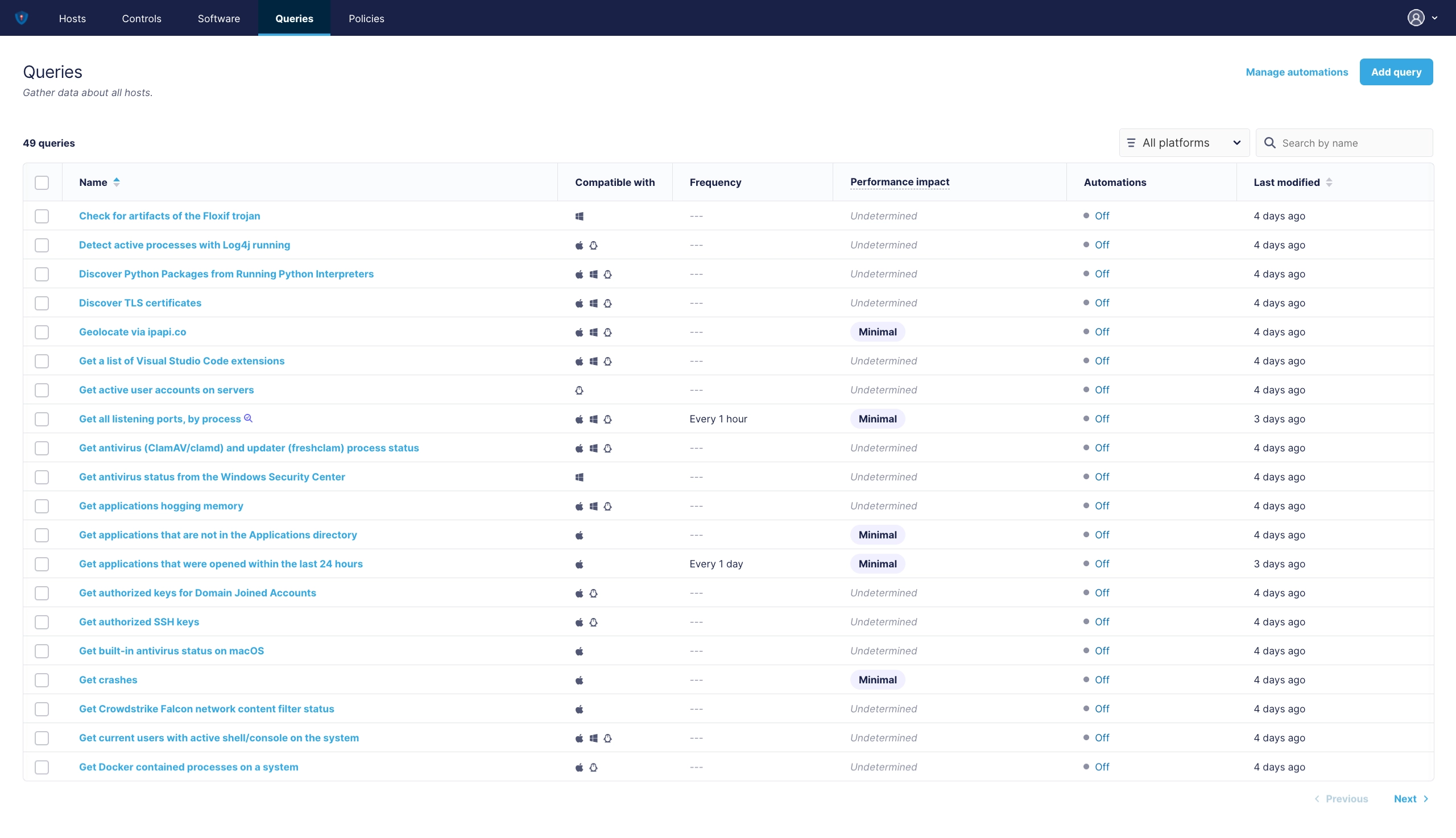
Like every SIEM or Cybersecurity Software, PVYdevices offers to create queries to all you host connected with PVYdevice Agent. Currently supported Operating Systems are:
- macOS
- Linux
- Windows
- ChromeOS
¶ Query Templates
With over 300 commonly used pre-built Queries, which can be automated, it offers a powerful solution ready to use out of the box after your hosts (Server, Docker, Enduser clients) are connected with PVYdevices Agent and/or with PVYmdm.
Where some of the basic queries match all Operating Systems, there are also OS Specific and Landscape specific queries available, for windows systems, macOS and Linux based Systems. You can query all of them to a single device or a host group to get the answers you are looking for and also assign a frequency, where this informations shall be queried with a defiined timer period.
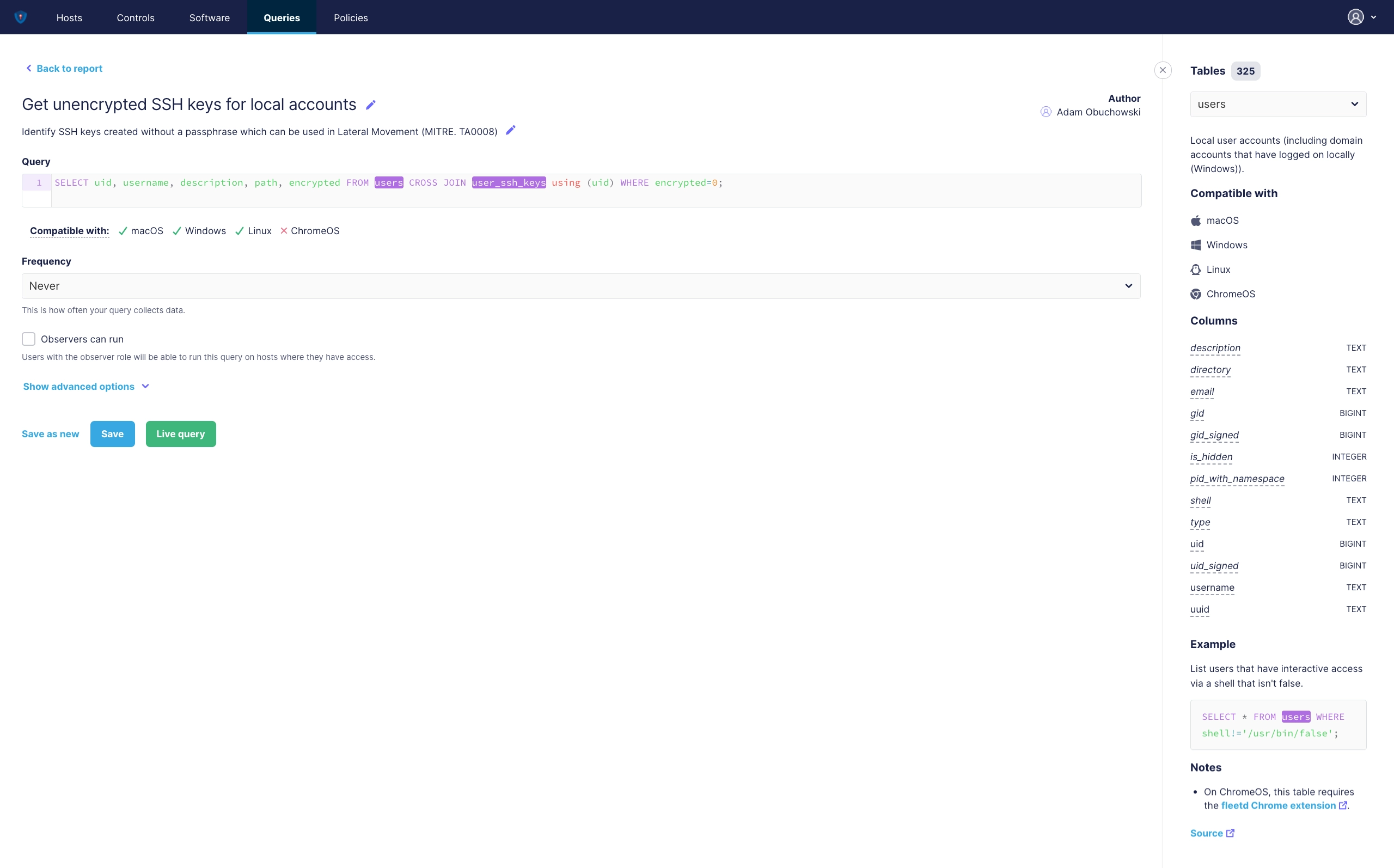
Like on Policies, you can not only create your own, you can also duplicate an existing once and make some changes to match some specific items, and save it as new one.
¶ Built-in Queries (300+):
- All OSquerie (Industry-default)
- Fleet Queries
- Palantir Queries
¶ Policies View
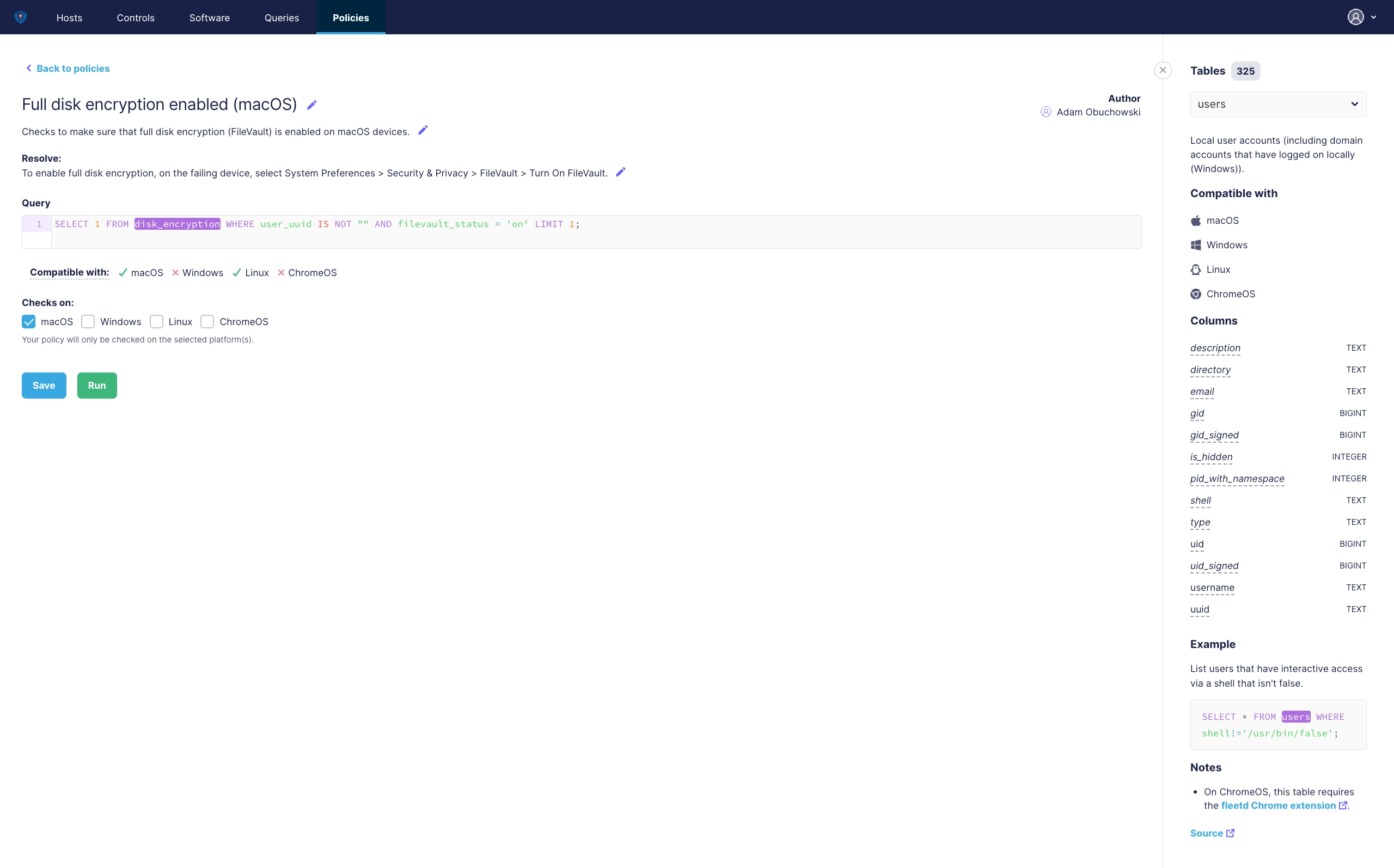
Every organisation has its default policies on several segments of their operations, commonly starting with Corporate Design and Document Guidelines, followed by Communication Guidelines among Employee Guidelines.
Unfortunally, a hugh percentage of small to midsize businesses believes, its not mandatory for them to have policies in their IT and Device Management, regardless if they run B.Y.O.D or having issued company devices to their employees or evven mix these strategies for cost reasons. Another percentage believes, that it’s sufficient to run some Anti-Virus and Internet Security Software.
When you point this out to this organization, you get the following answers from owner-managed companies as to why they don’t do it:
- Lack of Skills/Knowledge
- Cost factor
But here is the good news: While such Solutions like PVYdevices costs somewhere else almost $ 800 for 10 Users or above, PVYdevices is included in our PVVY@busiiness Subscription and above, with over 30+ other Applications and Services. Optionally you can ask for an SLA
And we all agree: It’s always cheaper, to have some Policies in effect, then having an incident, which leads not only to unproductivity, but becomes expensive to fix the mess afterwards.
You can use queries and policies with automatisation in two way:
¶ Without PVYmdm:
Automate Checks over Queries and Policies and notify both affected Users and IT SysAdmin, about a Policy Violation with User Interaction.
¶ Fully Automated with PVYmdm
When PVYdevices is connected with PVYmdm your PVYdevices Agents on the targeted hosts becomes your extended Arm. You can fully automate OS or Application Updates and correct any policy violation fully automated.
¶ What can be covered with Policies?
By default we deliver around 300 pre-defined Policies for macOS, Windows, Linux and ChromeOS, which checks the most important things in IT Management and let you monitor and automate that. Thanks to the built-in Policy Editor, which is based on the industry leading OSqery Open Source Projects, where defacto all Cyber Security Vendors lean on it, you can also build your own Policies. For example if you do Software or you have pushed an IoT Device to the market, you can include this over the PVYdevice Agent and create your underlining Policy for it.
¶ Automatic Incident Management
PVYdevices can be automated with external Service/Help Desk Software, to create a Incident Ticket each time a violation or an issue arrives.
¶ Status Web-hooks
You can create to any Domain as Target a Host Status Notification, with Informations about: Offline, came online, not seen since X days and so one. For example to PVYmessenger or to PVYserviceDesk. But also to PVYautomator.
¶ Integrations
¶ Service / Helpdesk / Support Software
Jira, Zendesk, PVYserviceDesk are being supported out of the Box
¶ Script Upload / Management
For each host, a .sh / .bash or power shell script can be uploaded. Either to perform manual or specific enrollments, cleaning up malware or system cleaning tasks.
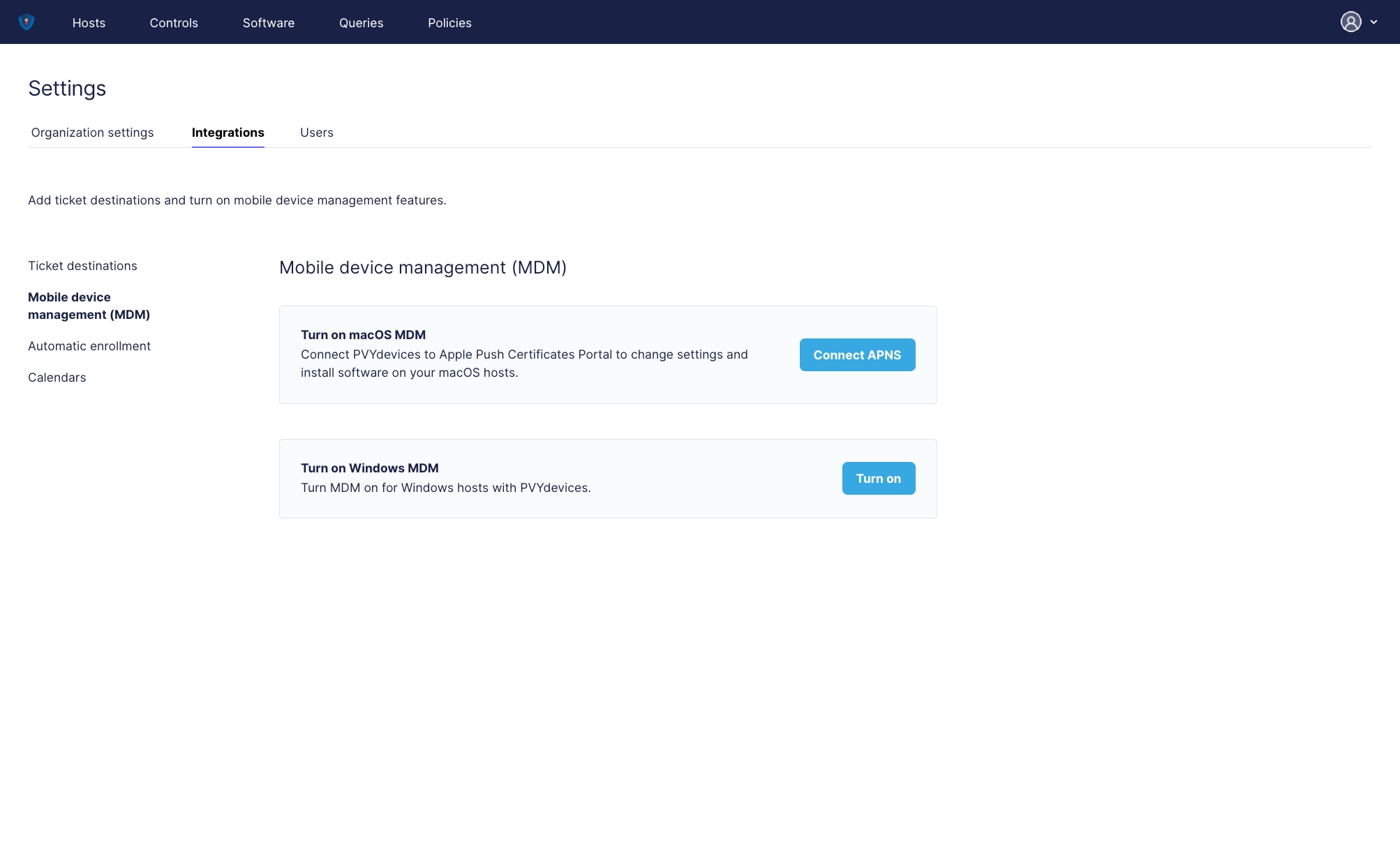
¶ MDM
PVYmdm for macoS, iOS and Windows Devices, with Apple APNS.
¶ Calendar
Schedule with User the targeted End user Device for Change-requests, Software Updates or Maintenance, which are not super crucial to get fixed immediate. The Support is give to PVYgroupware (CalDav).
¶ Automatic enrollment (beta)
which let you define which OS and Software Package shall be updated automatically by its availability, bonded to Policies.
¶ Device Management Strategies
There are a few common best practices out there, which has to be adopted to each Organisation Device and IT Landscape. Before you start, you need to consider to make an IT Inventory / Asset Audit or at least a spreadsheet to get a glimpse idea, if you may didn’t to that already. You may also want to check out PVYassets, which makes both world, the world of Accounting and ICT happy.
¶ Read the docs
¶ Settings & Account View
When launching PVYdevices for its firs time within your PVY@Cloud or PVY@Office using PVYcentral, most of the settings are bing being set. For E-Mail Notifications and Service Desk Ticket creation you have to enable and fill the Endpoints accordingly in «Settings - Organization Settings»
¶ F.A.Q
Q: Do I need IT Skills & Knowledge to benefit from PVYdevices ?
A: If you go only within the built-in Templates, you can manage the Queries and Policies. If you need to take certain problem solving actions without user interactions, such as scripting, its necessary that you know what you are doing. A common practice is to run PVYdevices in smaller organisation, which has for certain tasks in their IT duties an external supplier, who is skilled to support the need for the organisation.
Q: Can I book SLA or Managed Option on top if I feel not qualified?
A: Yes, PVY.swiss serve some Managed Service Provider and they can make you some offer. You can contact us for such Inquiries.
Q: Does PVYdevices / PVYmdm recognize a compromised UEFI or EFI Bootloader?
A: On macOS, special queries can indicate a Hackintosh or altered Bootloader based on KEXT comparisation. On Linux Baremetal Appliance and Windows not. Therefore, we have PVYutm available upon request, and PVYfirefall which works with the UTM. Please note, if you have an altered UEFI or EFI Bootloader, you have either an internal social engineering problem, or a supplier which has different interests than selling you hardware.
¶ Availablity
PVYdevices is available for PVY@Cloud and PVY@office Subscriber from the PVY@business Package. PVY Subscribers with lower subscription can book the Application within PVYcentral built-in Appstore, and the Application is getting deployed within your own PVY Personal Cloud Environment.