¶ PVYvault | Getting started
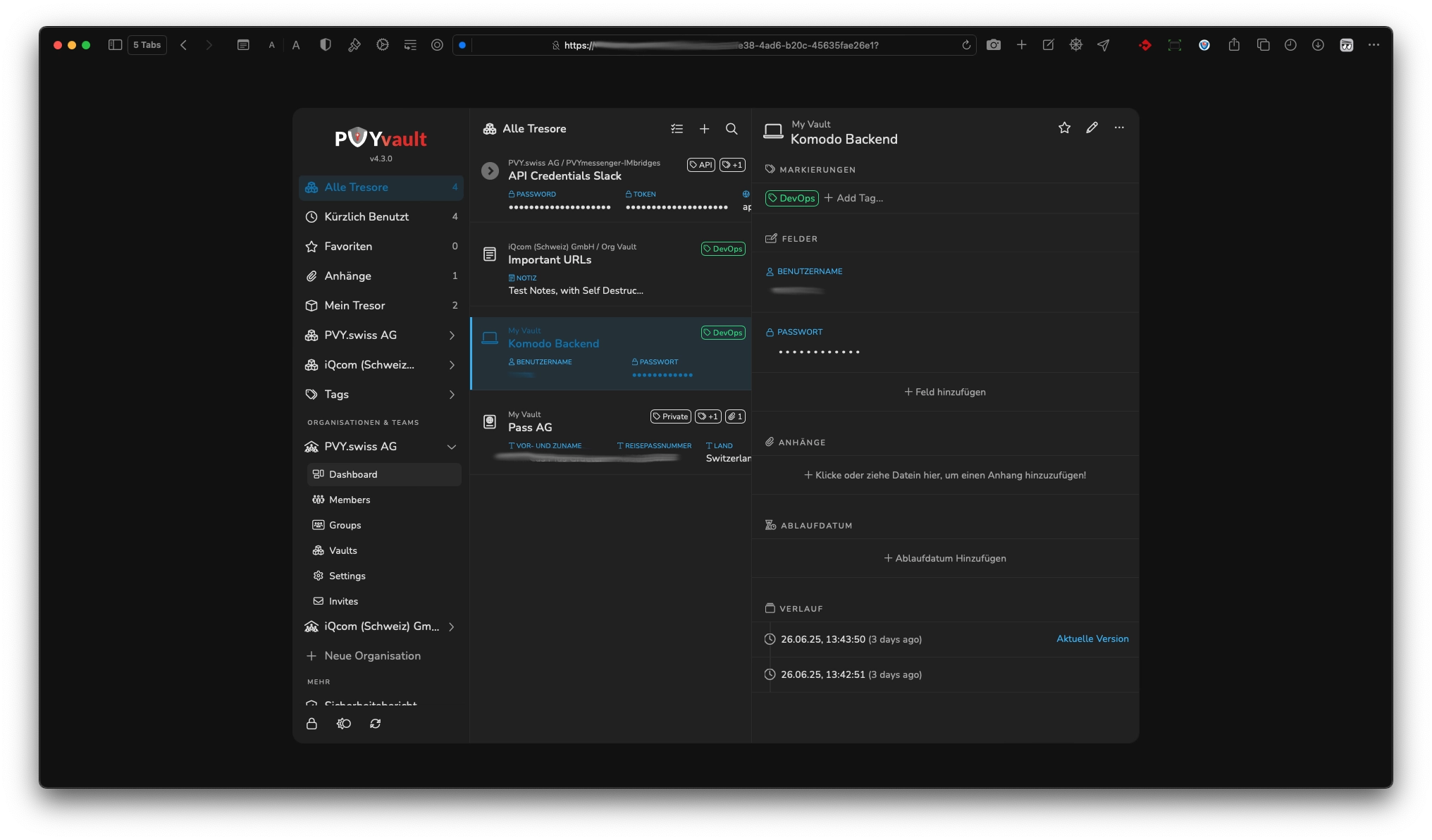
Cyber-Security starts on the User and Organisation Level. Storing Passwords and Secrets in a Cloud Storage, such as iCloud or Google, you neither don’t own, control and maintain, is an absolutely “No-Go”.
To take the pain of maintining, owning and using a truly secure and privacy focused Password Manager you can trust and use, we made PVYvault. And it’s best, it runs on your PVY@Home or PVY@Office Appliance, while PVY@Cloud Users can use our SaaS Edition for free for the entry level subscription, where Business and Enterprise Customers getting their own Vault on their own subdomain in their hermetically closed PVY@Cloud Environment delivered.
¶ PVYvault Feature Overview
PVYvault comes as Progressive Web Application with PVY-ID Single-Sign-On, Biometric Login Support for
- Windows Hello-ID plus MFA
- macOS Fingerprint Unlock plus MFA
- iOS Facetime Unlock plus MFA
and offers you beside a ultra-fast Web Application with Browser Extensions for:
- Chrome
- ZenBrowser
- Opera
- Brave
- Firefox
- Orion
- Safari
- Edge
also a Desktop Application with the same Features for:
- Linux
- macOS
- Windows
and Mobile Apps for
- iOS
- Android
- GrapheneOS
- eOS
an All-on One Solution to manage your secrets securely 4096bit encrypted across your Devices. You can use the Apps even you are offline or in a Network, which does not allow outside communication due it’s built-in Sync and Local First Feature.
Creation of Secrets/Password Objects with built-in Templates for:
- Website/WebApp
- Computer/Server
- WiFi Access
- Note (Rich Text & Markdown Support, Editor, small and fullscreen)
- Document
- Bank Account
- Passport/ID Card
- Database
- SSH Key Pair
- API Tokens & Secrets
- Web-hooks
- Authentificator
- Password Generator
- Custom defined
All Objects can contain one or more secrets, can be enhanced with an attachment and you can add beside of Tags for Classification / Organisation of your Objects as well Custom Fields for each of them. You also can set an optional Expiry date for an object and PVYvault will warn you over the built-in security report, that an object is expiring soon. This feature can be used either for official documents, such as Passports, ID or Credt Cards, to remind you to update these credential or order a new one, or you can use it for a controlled manual credential rotation.
Objects are stored either in
- Personal Vaults
- Organisation Vaults
For each of them, you can create multiple Vaults, which is in General not an bad idea. (See our Guideline for enhanced Online Privacy and Security below in the “Read the Docs” Section.
Please note, the PVYvault Web Browser Extension always try to match available Fields for Auto-Fill when you are in an Online Store and want to use your credit card, or buying a flight ticket. However, if the fields not matching, since the specific developer of the visited page use special identifier and not standard identfifiers, the extension let you browse possible matches.
¶ Creation and Management of Personal Vaults
You can create as many personal vaults as you like. Objects stored in a personal vault can’t be shared with other members you have in one or more Organisations. You can import or export your objects, tag them. We highly recommend to have different vaults, for example for different E-Mail Addresses / Identities you use in the Web. Having your Secrets organised in different vaults, such as:
- Travel
- Shopping
- Finance
- Social Media
- Forums/Community
Minimize not only your digital footprint with a trace back of your real identity regarding privacy and data brokering, it helps you also to streamline your digital activities in a more organized way. Ideally you have different email addresses for each of your online activities, not only using an “Alias” to one E-Mail Provider.
Tip: If you want to share a personal password with some one else, copy it and send it over our secure PVYmessenger. If you want to share it permanently, you can move this Object to your Family or Organisation Vaults of choice, with a simple click.
¶ Creation and Management of Organizations
You can create one or many Organisation and within an Organisation you can invite other PVY-ID Users to forma a Team or Group of Users, where a specific Vault or Tresor Object can be shared. Shared with Permission such as:
- Read only
- Can modify
- Owner
So you can organize your Vauls within an Organisation as your Organisation is organized, and adding Vaults, such as, Procurement, Sales, Informatic, DevOps, SysAdmins as for example, and segment it even further with the Team Functionality to restrict in a Vault Stored Objects Object based only to the Team DevOps.
¶ Organization Dashboard
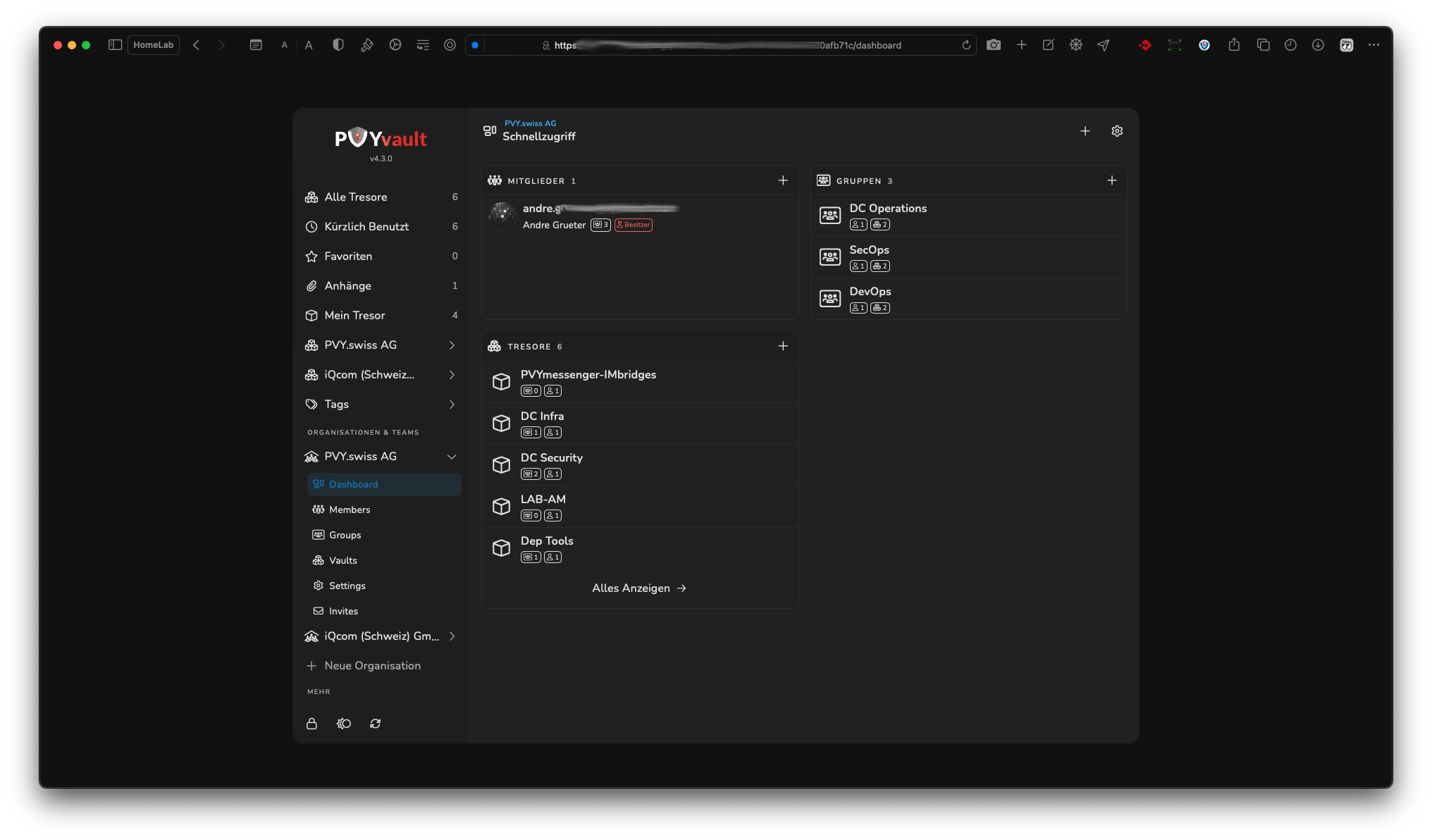
Each added Organization sports a Dashboard to give you a quick overview, what inside this Organisation, such as how many Vaults created, their names, the Groups amd Members of each Group. You can inspect the things quickly this way.
¶ Organisation of Members / Users
¶ Creation and Management of Organization Vaults
You can create as many vaults for personal or organization as you like. You can also shift entire vaults objects any of your vaults to another vaults, such as selected or all Objects from My Vault to an Organisation Vault XY.
You can also search for objects stored in Vaults, in the Web App or Desktop and Mobile App, but as well in the Browser Extension.
Objects in your Vault you can tag, rename, add custom fields, add pre-defined fields such as:
- Username
- Password/Secret
- Emailaddresse
- URL
- Date
- Month
- Credit Card Number, Security Code, Due Date
- Phone Number
- Pin
- Plaintext
- Richtext / Markdown
- One Time Password (OTP)
In short, you can also add Instruction as Rich Text or copy from a Wiki Entry Content in Mark Down Language and add it as Note, an alter the Title “Note” into “Instructions”.
¶ Built-in Version Control and Audit Logs
Each saved Object underlies according to ISO 27001 an automatic Version Control, displayed as History and inlcuded Audit Logs for Organizations, so you can easy identify, which PVY-ID User has changed a Group or protected Object.
The History let you also revert to a previously state of a stored object. This can become very handy, for example a use case almost any System-Administrator once in Life run into it:
You like to rotate the Credentials for certain reasons, generated and saved new ones in the Password Manager, but forgotten to login before to the Host or Client, to change it. Thanks to Version Control, you can roll-back and forth.
¶ Multifactor (MFA) and Biometric Authentification Support
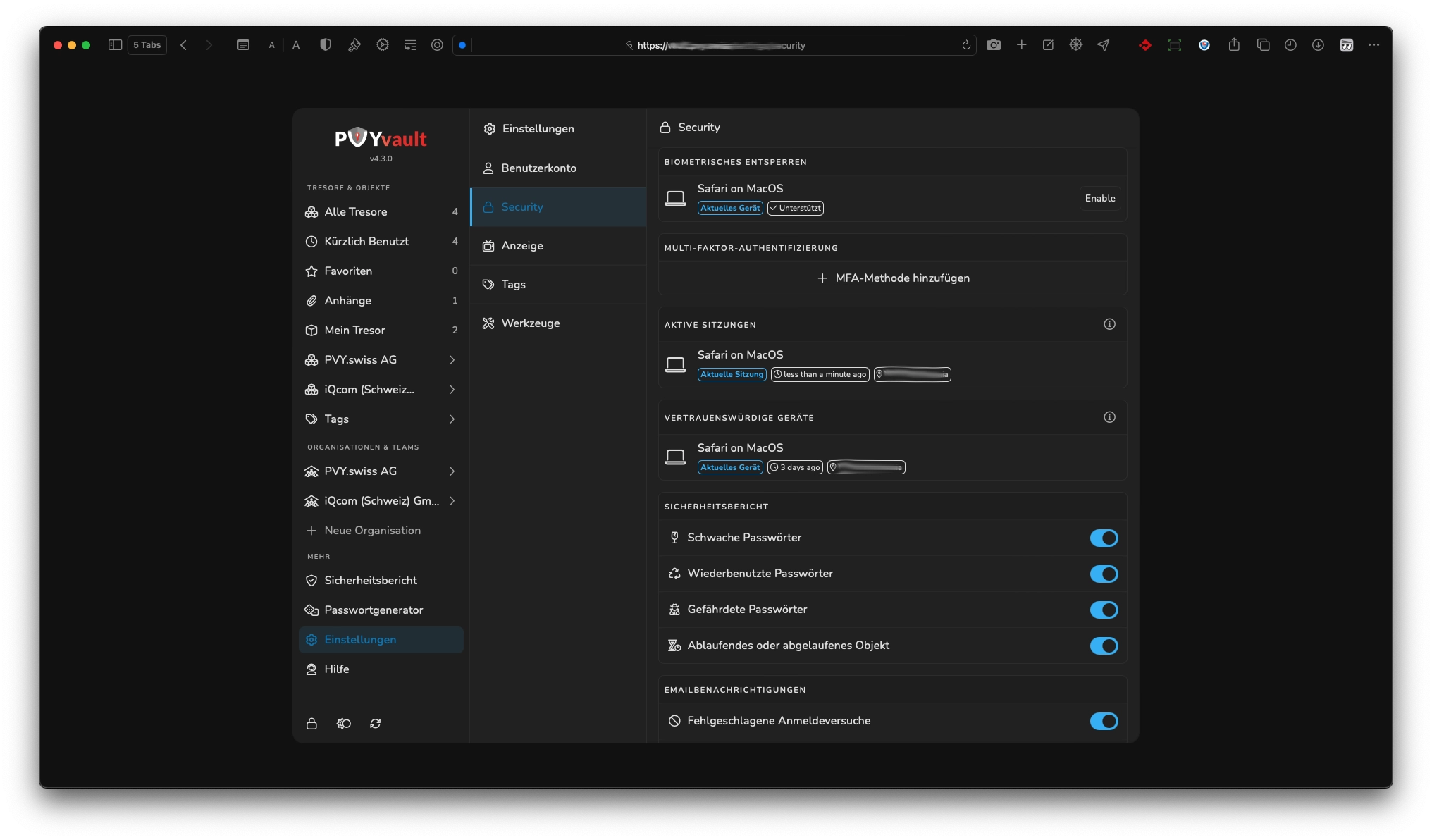
¶ Biometric
Biometric Authentifcation Unlock Support for Windows Hello-ID, macOS Facetime/Fingerprint can be enabled Device Specific. It works for the Web App as well for Desktop/Notebook and Mobile Apps.
¶ Hardware Key Support (IDEM/FIDO2)
- Yubikey USB
- Google Titan
- BitBox02
- Kudelsky
¶ TOTP
- FreeOTP
- Google Authenticator
- Authy etc
Please note, you need to have on your Smartphone a QR Code capable OTP/TOTP Authenticator. If you enable this, you need to scan and confirm the verification OTP code to activate this additional Layer of Security.
Please note, for stored Objects, you can also add TOTP Field for other Web Apps/Websites. This is not connected to your local OTP/TOTP Authenticator. The aim to add this TOTP for other Websites or Apps is for the sake of sharing this Object with your Team Members in a specific Vault, so they can login using the correct from PVYvault Issued TOTP/OTP Code and do not need to ask the creator of this Login, to share a timely sensitive OTP Code.
¶ Migrations from other Password Manager easy made
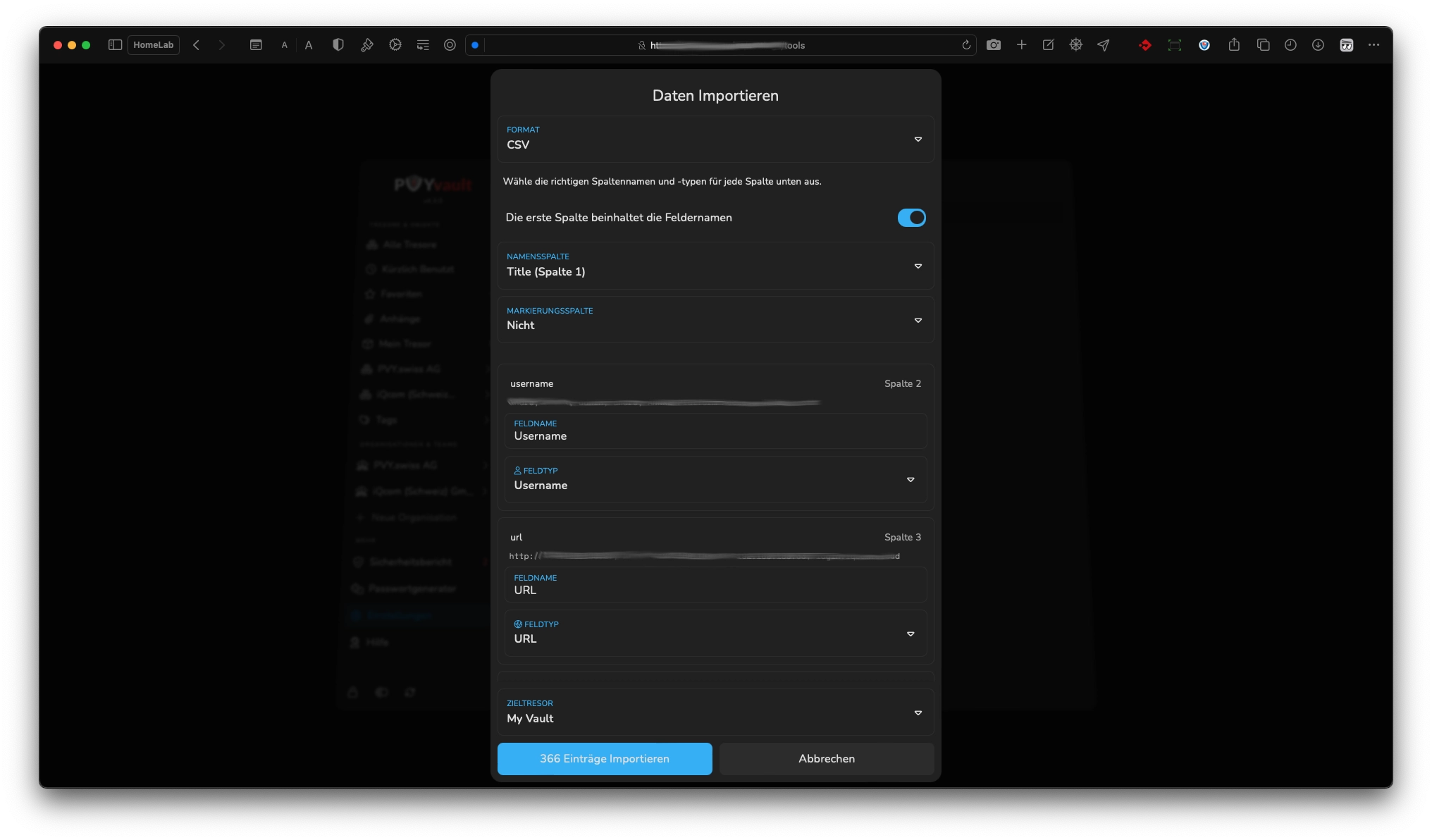
Thanks to pre-defined Import Templates for:
- Any .csv File
- 1Password (1pux,csv)
- Lastpass
- KeePass (csv)
- Keyguard (json,csv)
- Bitwarden (json)
- Passbolt (csv)
- Nordpass (csv)
- iCloud (csv)
- macOS Keychain (csv)
- Chrome (csv)
- Firefox (csv)
- Orion (csv)
You perform a Migration from any of these other Password Manager Solutions to PVYvault within 5-10 Minutes or less. You can also streamline and prune your previous Password Manager Export in PVYoffice as Spreadsheet first, remove clutter, and map the fields quickly on upload. That easy.
¶ Navigation
¶ Vaults & Objects
- All Vaults (Al Objecst of your Personal and allocated Organizatoin Vaults)
- Recently used
- Favorites
- Attachments
- My Vault
- My Organizaton LLC1
- List of Vaults
- My Organisation LTD2
- List of Vaults
- Tags
¶ Organizations & Teams
You can manage more than one Organization / Company and each of them can have different Team Member and secure Vaults.
¶ Organizaton LLC1
- Dashboard
- Members
- Groups
- Vaults
- Settings
- Invites
While the Dashboard, Member and Group Settings are self-explaining, you need to use the Invites Menu to Invite your PVY-ID User(s) to your Organisation, once they joined, you can organise them into groups or grant permissions to stored Vaults or stored Objects in particular. Each Invite Operation is limited to 50 PVY-ID E-Mail Addresses. Please note, for security reasons, you can not invite external users which are not within your specific Organisation Domain if you are using PVY@Home, PVY@office, PVY@businsess or PVY@enterprise deployment. However, for the free PVYvault SaaS Version, you can invite other PVY-ID users to share a Password. Please note, the Invited Person has to accept the Invite and complete this Invite by log in into PVYvault.
In the Setting you can enable or disable the Synchronisation of your Organization Directory you can enable Active Directory Synchronisation for your Users. This feature only works, if you have an active PVY@enterprise Subscription, and using PVY-ID with NIS2 Hyprid Option connected to your “On Premise Infrastructure”. Otherwise, do not activate this Feature. It allows you instead to send out E-Mail Invites, to add Users from Browsing your User Directory on your Master Active Directory Server to a specific Group or Vault.
¶ Organisation LTD2
- Dashboard
- Members
- Groups
- Vaults
- Settings
- Invites
¶ More
¶ Security Report
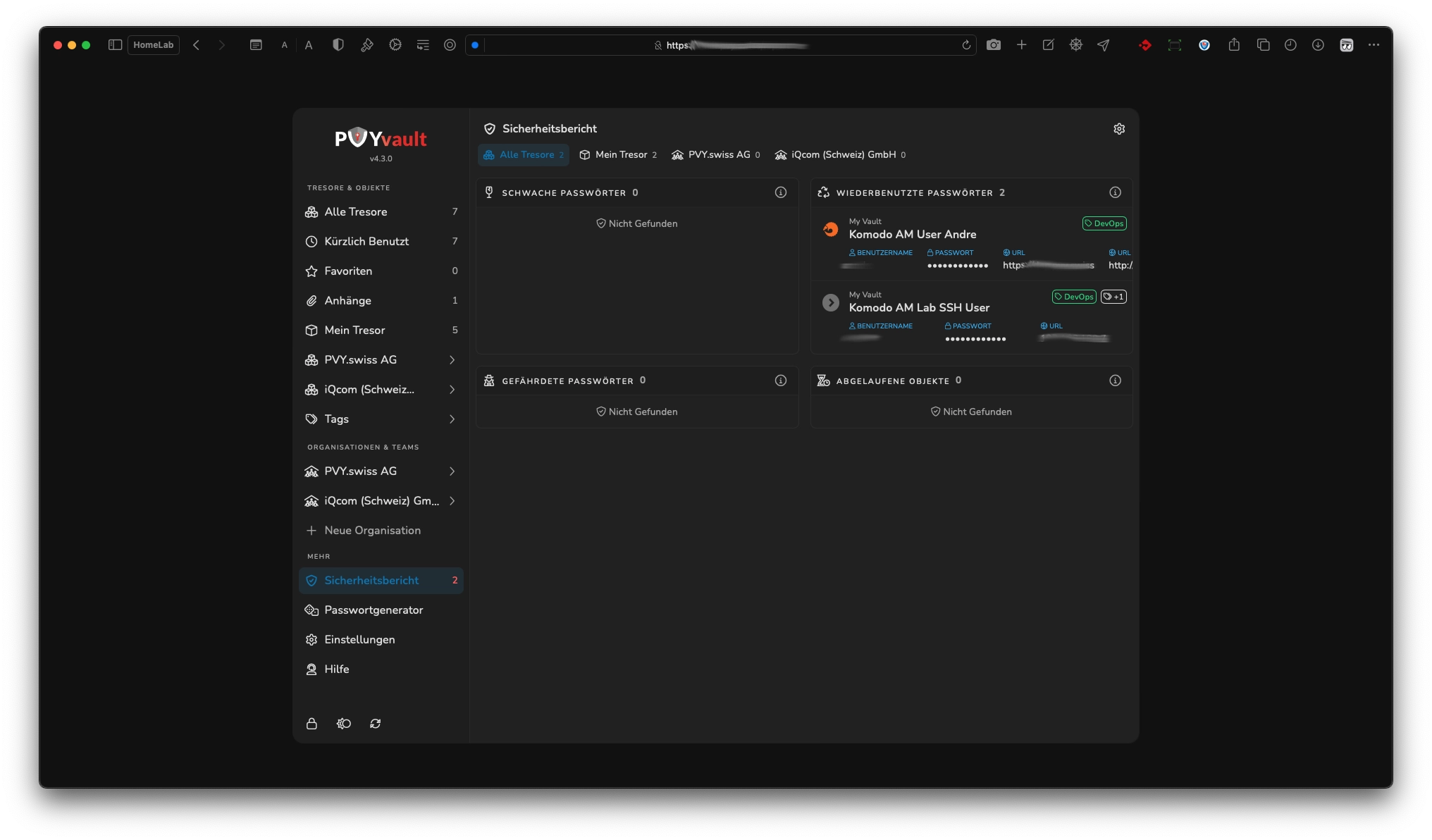
To raise the awareness to your organization and its user, why Passwords have to be maintained in a secure and profen way, we included an API Download Query for Pawned Passworts, from https://api.pwnedpasswords.com where all cyber-security organizations and ethical hackers are reporting any Darknet or Hacked /Leaked Data of Usernames and Passwords.
PVYvault is not uploading your stored objects there, its downloading every 30 Minutes their database, and performs a local query against your stored passwords / usernames. If there is any match or a weakness given to a similar password already used in hacking attempts, the Security Report warns you and your users about, to change certain passords.
¶ Password Generator
The Password Generator is very simply designed, to give you the option to generate either a word-phrase or using Characters with a certain composition and lenght to generate a new token or password for a signup you want to do.
¶ Settings
¶ User Account
Here you can delete your User Account. Please note, deleting an account is irreversible. All your created objects are being erased and your account is truly deleted from the systems and not only flagged with a 0 in the database.
If you are using our awesome PVYbackup optionally, you can restore a snapshot from one our earlier. Just check if there are other passwords generated meanwhile, and export them before, before you travel back in time.
¶ Security
Here you will find some additional Security Features for MFA, Biometric Unlock, Active Sessions and Trused Devices.
¶ Automatic Lock
Set the Time over the Slider, after how many minutes of idle time, the PVYvault logs you out.
¶ Biometric Unlock
Enable Biometric Unlock using Fingerprint Methology on Desktop / Notebooks who sports a TMP 2.0 or higher Security Chip on the Device, or for Smartphone with Facetime.
¶ Active Sessions
Lists all your current active session, Device, Browser, Location such as City and Country current logged in, with option to void the Session.
¶ Trusted Devices
You can add, both on the Web Browser or in the PVYvault App Devices as Trusted. If the PVYvault App logs you out due iddle time, the Username is visible and let you quickly re-login using either your Password/Passphrase or Biometric Authentification.
¶ Security Report
Personalized Setting about exipring Objects, Passwords in use classifed as weak, leaked and pawned. It also warns about re-used passwords, which needs to be avoided.
¶ Email Notification
You can enable E-Mail Notification for:
- Failed Login attempts
- New Sign-ins from untrusted Devices
Maybe, if requested, we can enable later Push Notificatons to PVYmessenger.
¶ Display
Theme, dark, light or automatic based on your OS Settings. Default is Automatic. You can enable or disable the automatic loading of Favicons. This can be helpful for certain user to get a better visual identification of stored Objects in Vault, since the Favicon is mostly the Brand Logo of a Website, Webapp or Online Shop. However, you will leave a short minor trace in the Analytics of the specific Website or Web App: When PVYvault is downloading and adding the Icon to the Object, it shortly reveals the IP of your PVYvault. They may don’t notice this single connect within a fraction of a second, but every Web Server will have an access log of such things (We mention this only for super paranaoid power user).
¶ Tags
Manage your Tags for Object Classification / Organisation and change Colour, Name or Unlist a certain tag.
¶ Tools
Import and Export of your Passwords. You can export your password in an encyrpted Container (secure) or as .csv File (unsecure and plain). Further more you can import from with pre-defined Import Templates from:
- Any .csv File
- 1Password (1pux,csv)
- Lastpass
- KeePass (csv)
- Keyguard (json,csv)
- Bitwarden (json)
- Keyguard (csv)
- Passbolt (csv)
- Nordpass (csv)
- iCloud (csv)
- macOS Keychain (csv)
- Chrome (csv)
- Firefox (csv)
- Orion (csv)
For any other sources, you can match your column name easely with the built-in assistant. A typical Migration from another Password Manager to PVYvault is performed under 10 Minutes. Hint: Import them into “My Vault” and shift them after accordingly to other shared or non-shared Vaults on PVYvault.
¶ Help
Under help you will find Quicklinks to our Documentation as User Manual (here), Support Contact, HelpDesk Blog and our Official Website, Terms of Service and Privacy Policy.
¶ Read the Docs
PVYvault Web App is designed with offline / local first approach. This means, even you lose internet connection and the read bar on the Web App indicates you, that you are offline, let you authenticate again if you got logged out and you can browse your vaults and its objects with full functionality.
You can also save it as a fully functional Web App to your Desktop or Mobile App, in case you don’t want to use the Desktop or Mobile Apps.
To download the Web Extension for your favorite Browser, please visit:
¶ Web Browser Extension
| Browser | Url |
|---|---|
| Chrome, Orion, Opera, Brave | https://vault.yourdomain.tld/pvyvault-chrome-signed.zip |
| Firefox, Zen | https://vault.yourdomain.tld/pvyvault-firefox-signed.xpi |
| Safari | App Store for Extensions, Search PVYvault (Generic) |
| Microsoft Edge | https://vault.yourdomain.tld/pvyvault-edge-signed.zip |
The extensions are properly signed. Download them and add it manually or add it with the Browser prompt.
A note for Apple Safari Users. We highly recommend the Web Browser Orion RC. Then use the PVYvault-Chrome Extension, which has been optimized to work with Orion RC and Orion Community Web Browser. It’s like Safari, but just on a another Level. Also availale for Linux, iOS and Android.
The Safari Extension inludes a “Server-URL” Field, which you need to enter with “https://vault.yourdomain.tld/server” while the other extension are being automatic built and deployed when PVYvault is being deployed on your PVY@Cloud, PVY@Home or PVY@Office Appliance. It comes with a Checksum against your PVYvault Application and Users simply can authenticate without Configuration using their PVY-ID and optinonally either Biometric, USB-Key based, or TOTP/OTP Code.
¶ Desktop and Mobile Apps
Visit our App Directory Website under https://pvy.app and click on the PVYvault Section with your targeted Device the Download Icon. It will redirect you based on your OS automatically to your OS specific App Store or initiate a download if you are Debian or Redhat User. Mobile Apps also includes an F-droid Link for anonymous deployment.
¶ Updates
If we push an update, you will find for the Browser Extension with the Links above the new Version automatic. Mobile and Desktop apps are updating automatic if set to true in your App Store settings. Linux user needs to perfom an update manual by removing the elderly version and download the new one.
¶ No Backdoors - No overrides - No Telemetry Data
Like every PVYapp, there are no Analytic Data or Telemetry Data being sent back to us. We also can ensure, there are no Backdoors implemented. Database entries are not only hashed, they are encrypted. Attachements and Documents stored in PVYvault are being encrypted and stored in a special mounted Volume (Encrypted Disk-Image) for each Deployment. To speed up the Application responsivness, we also included a volume for static assets to make the Progressive Web App super snappy to work also with bad internet connections.
The reason we do not integrate attachements or documents into the encrypted Database and chosen a File Store method is simple. We don’t want to blow up the database.
¶ Encrypted Deployment Credentials
Credentials used for each deployment of the Server Component, the Frontend PWA Components and to the Postgres Database are encrypted using getops while each of our Customers Deployment is being built. On top, we use configu, which issues over getops on a regulary schedule new credentials and rotates them.
¶ Non-priviliged Container.D and Non-privilged Docker/Pods
Each of our Deployment is non-priviledged on all Levels. Each Application Stack has its own Network. Each Customer its own VLAN seperated hermetically sealed PVY@Cloud or PVY@Home/Office Environment.
¶ Accessible via PVYvpn only
You can choose on Deployment Option (already on Signup for PVY@Cloud) if you would like to use it only with PVYvpn. Choosing this dead-secure option, makes the Application only available behind our amazingly fast PVYvpn and not on the Public with SSL Port 443. You can add in PVYcentral, Tab Security, Management IPs, so in case there is a once Problem on PVYvpn Services on your own instance (never occured one in production past 5 years) to have granted IPs who can access PVYvault in an Emergency without a running PVYvpn.
This section provides a high level overview of the security design and architecture of the PVYvault application.
¶ Security Principles
¶ Simplicity
While the secure processing, storage and sharing of sensitive data necessarily involves a certain degree of complexity, PVYvault tries to hide this complexity from the end user as much as possible. In other words, users should be able to use the application securely without understanding (or even being aware of) the underlying security principles. At the same time, the applications inner workings and security mechanisms should be easily verifiable by those who have the technical knowledge to do so, which brings us to…
¶ Transparency
It is a widely know fact among security experts that Security through Obscurity is not only ineffective, but can in fact be harmful if used to cover up otherwise sloppy security practices. We believe that full transparency is not only the best foundation for trust, but also allows us and other independent reviewers to discover and fix any potential security flaws and efficiently as
quickly as possible.
¶ No Trust Required
While PVY.swiss open source nature is helpful in uncovering unintended vulnerabilities in the source code, it is, by itself, insufficient for verifying that the code actually deployed in production is not altered in a way that may compromise the security of the application either intentionally or unintentionally. This is why we take additional steps to make sure that some parts of the architecture can in fact be verified in production, while others do not need to be verified by design (see Possible Attack-Vectors And Mitigations).
This means that unlike other products, PVYvault does not require explicit trust between the end user and the host.
¶ Encryption
Robust data encryption is the foundation of PVYvault security architecture. PVYvault utilizes three basic encryption schemes.
¶ Simple Symmetric Encryption
This is the most basic encryption scheme used in PVYvault. Simple encryption employs a symmetric cipher to encrypt the provided data with a randomly generated key. The encrypted data, along with the encryption parameters needed
for decryption, is stored in a container object, which can then be stored or transmitted securely. PVYvault currently uses the AES cipher in GCM mode, but other options may be added in the future.
¶ Encryption
- Choose a random encryption key
k - Choose a random initialization vector
ivand additional dataa(for
authenticated encryption modes) - Generate the encrypted data
c = AES_encrypt(k, p, iv, a)from the plain
textp - Store
c,ivandain the containerC
┌───────────┐ ┏━━━━━━━━━━━━━━━━┓
========= │ │ ┃Simple Container┃ ╔═══════════╗
== key ==─────┘ ▼ ┃ ┃ ║ encrypted ║
========= ┌─────────┐ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃ ╚═══════════╝
│ encrypt │ ┃ encryption │┃ ┌ ─ ─ ─ ─ ─ ┐
┌────▶│ (AES) │────────────▶│ parameters ┃ plain
│ └─────────┘ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃ └ ─ ─ ─ ─ ─ ┘
============== │ │ ┃╔══════════════╗┃ =============
= plain text =────┘ └─────────────────▶║encrypted data║┃ = ephemeral =
============== ┃╚══════════════╝┃ =============
┗━━━━━━━━━━━━━━━━┛
¶ Decryption
- Let
kbe the key used for encryption. - Retrieve
iv,aandcfromC - Generate the plain text
p = AES_decrypt(k, c, iv, a)
¶ Password-Based Encryption
In the password-based encryption scheme (based on the PBES2 standard) an encryption key is derived from a user password using the PBKDF2 key derivation function.
¶ Encryption
- Choose a password
p - Choose an iteration count
iand random salts - Generate
k = PBDKF2(p, s, i) - Choose a random initialization vector
ivand additional dataa(for
authenticated encryption modes) - Generate the encrypted data
c = AES_encrypt(k, p, iv, a)from the plain
textp - Store
s,i,c,ivandain the containerC
============ ┌────────┐ ┏━━━━━━━━━━━━━━━━┓
= password =──────────▶│ PBKDF2 │───────┐ ┃ Password-Based ┃
============ └────────┘ │ ┃ Container ┃
│ │ ┃ ┃
│ │ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃
▼ │ ┃ PBKDF2 │┃
========= └──────▶│ parameters ┃
== key == ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃
========= ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃
│ ┃ encryption │┃
▼ ┌──────▶│ parameters ┃
┌─────────┐ │ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃
============== │ encrypt │ │ ┃╔══════════════╗┃
= plain text =─────────▶│ (AES) │──────┘┌─────▶║encrypted data║┃
============== └─────────┘ │ ┃╚══════════════╝┃
│ │ ┗━━━━━━━━━━━━━━━━┛
│ │
└────────────┘
¶ Decryption
- Let
pbe the password used for encryption - Retrieve
s,ifromC - Generate
k = PBDKF2(p, s, i) - Retrieve
iv,aandcfromC - Generate the plain text
p = AES_decrypt(k, c, iv, a)
¶ Shared-Key Encryption
Shared-key encryption is used to securely share sensitive data between a number of independent accessors without the need for them to share a common password.
This encryption scheme is loosely based on the JSON Web Encryption specification where a shared symmetric encryption key is individually encrypted with each accessors public key and stored alongside the encrypted data. Accessors can then access the data by using their private key to decrypt the AES encryption key which is in turn used to decrypt the original data.
¶ Encryption
- Generate a random encryption key
k - Choose a random initialization vector
ivand additional dataa(for
authenticated encryption modes) - Generate the encrypted data
c = AES_encrypt(k, p, iv, a)from the plain
textp - Let
[A_1, A_2, ..., A_n], A_n = { id_n, pub_n }be a number of desired
accessors wherepub_nis the accessors public key andid_na unique
identifier. - For each accessor, generate
K_n = RSA_encrypt(pub_n, k) - Store
c,iv,a, andK = [{ id_1, K_1}, ..., {id_n, K_n}]in container
C
┏━━━━━━━━━━━━━━┓ ┌───────────────────────────────────────────────────────────┐
┃ Accessor A ┃ │ │
┃ ┃ ▼ ┏━━━━━━━━━━━━━━━━┓ │
┃┌ ─ ─ ─ ─ ─ ─ ┃ ┌─────────┐ ┃Shared Container┃ ============== │
┃ public key │─────┐ │ encrypt │ ┃ ┃ = plain text = │
┃└ ─ ─ ─ ─ ─ ─ ┃ └─────▶│ (RSA) │─────┐ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃ ============== │
┃╔════════════╗┃ └─────────┘ │ ┃ encrypted │┃ │ │
┃║private key ║┃ └─────▶│ key (A) ┃ ▼ │
┃╚════════════╝┃ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃ ┌─────────┐ │
┗━━━━━━━━━━━━━━┛ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃ │ encrypt │ =========
┃ encrypted │┃ ┌───│ (AES) │◀────== key ==
┌─────▶│ key (B) ┃ │ └─────────┘ =========
│ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃ │ │ │
┏━━━━━━━━━━━━━━┓ │ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃ │ │ │
┃ Accessor B ┃ │ ┃ encryption │┃ │ │ │
┃ ┃ │ ┃│ parameters ◀─┘ │ │
┃┌ ─ ─ ─ ─ ─ ─ ┃ ┌─────────┐ │ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃ │ │
┃ public key │─────┐ │ encrypt │ │ ┃╔══════════════╗┃ │ │
┃└ ─ ─ ─ ─ ─ ─ ┃ └─────▶│ (RSA) │─────┘ ┃║encrypted data║◀──────────┘ │
┃╔════════════╗┃ └─────────┘ ┃╚══════════════╝┃ │
┃║private key ║┃ ▲ ┗━━━━━━━━━━━━━━━━┛ │
┃╚════════════╝┃ │ │
┗━━━━━━━━━━━━━━┛ └───────────────────────────────────────────────────────────┘
¶ Decryption
- Let
id_n,priv_nbe the id and private key of one of the accessors used
during encryption. - Retrieve
KfromC, find the encrypted keyK_nforid_n. - Generate
k = RSA_decrypt(priv_n, K_n) - Retrieve
iv,aandcfromC - Generate the plain text
p = AES_decrypt(k, c, iv, a)
┌─────────┐
┏━━━━━━━━━━━━━━┓ │ decrypt │ ┏━━━━━━━━━━━━━━━━┓
┃ Accessor A ┃ ┌─────────▶│ (RSA) │◀────────┐ ┃Shared Container┃
┃ ┃ │ └─────────┘ │ ┃ ┃
┃┌ ─ ─ ─ ─ ─ ─ ┃ │ │ │ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃
┃ public key │┃ │ │ │ ┃ encrypted │┃
┃└ ─ ─ ─ ─ ─ ─ ┃ │ ========= │ └─────────│ key (A) ┃
┃╔════════════╗┃ │ == key ==◀─┘ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃
┃║private key ║─────────┘ ========= ┌───────────┐ ┃┌ ─ ─ ─ ─ ─ ─ ─ ┃
┃╚════════════╝┃ │ │ │ ┃ encryption │┃
┗━━━━━━━━━━━━━━┛ │ ▼ └──────│ parameters ┃
│ ┌─────────┐ ┃ ─ ─ ─ ─ ─ ─ ─ ┘┃
│ │ decrypt │ ┃╔══════════════╗┃
└──────▶│ (AES) │◀────────────║encrypted data║┃
└─────────┘ ┃╚══════════════╝┃
│ ┗━━━━━━━━━━━━━━━━┛
▼
==============
= plain text =
==============
¶ Client-Server Architecture And The Zero-Trust Principle
[[TODO]]
¶ The Account Object And Master Password
The Account object represents an individual PVYvault user and is central to PVYvaults encryption and authentication mechanisms. Each Account holds the following information:
- The user’s email address is not only used as a communication channel
but, more importantly, serves as a unique, human-verifiable identifier for
each PVYvault user. - A RSA private key and public key pair is used in places where a user
needs to be granted access to data protected via the
Shared-Key Encryption Scheme. - A HMAC key used for signing and verifing organization details (see
Organizations And Shared Vaults / Adding Members - A unique, immutable id
- A (display) name
The Accounts private key and organization signing key are considered secret and should only ever be accessible to the Account owner themselves. They are therefore encrypted at rest using the Password-Based Encryption Scheme with the users Master Password serving as the secret passphrase.
┏━━━━━━━━━━━━━━━━━━━━━┓
┃ Account ┃ ╔═══════════╗
┃ ┃ ║ encrypted ║
┃ ┌ ─ ┐┌ ─ ─ ┐┌ ─ ─ ┐ ┃ ╚═══════════╝
┃ id name email ┃ ┌ ─ ─ ─ ─ ─ ┐
┃ └ ─ ┘└ ─ ─ ┘└ ─ ─ ┘ ┃ plain
=================== ┃ ┌ ─ ─ ─ ─ ─ ─ ─ ─ ┐ ┃ └ ─ ─ ─ ─ ─ ┘
= Master Password =───────┐ ┃ public key ┃ =============
=================== │ ┃ └ ─ ─ ─ ─ ─ ─ ─ ─ ┘ ┃ = ephemeral =
│ ┃ ╔═════════════════╗ ┃ =============
decrypts ┃ ║ ┌─────────────┐ ║ ┃
│ ┃ ║ │ private key │ ║ ┃
│ ┃ ║ └─────────────┘ ║ ┃
└───────▶║ ┌─────────────┐ ║ ┃
┃ ║ │ signing key │ ║ ┃
┃ ║ └─────────────┘ ║ ┃
┃ ╚═════════════════╝ ┃
┗━━━━━━━━━━━━━━━━━━━━━┛
¶ Vaults
A password managers core functionality is the secure storage of sensitive data like passwords, credit card details and or any other kind or data a user may want to protect from prying eyes. In PVYvaults, this data is stored within so-called Vaults or in German: Tresors.
A Vault is basically a container object that employs the Shared-Key Encryption Scheme to encrypt and store sensitive data in a way that makes it accessible to only a number of specific users, represented by their corresponding Account objects.
┏━━━━━━━━━━━━━━━┓ ┏━━━━━━━━━━━━━━┓
┃ Account ┃ ┃ Vault ┃
┃ ┃ ┃ ┃
┃ ┌ ─ ─ ─ ─ ─ ┐ ┃ ┃ ╔══════════╗ ┃
┃ public key ──────encrypts──────▶║vault data║ ┃
┃ └ ─ ─ ─ ─ ─ ┘ ┃ ┃ ╚══════════╝ ┃
┃ ╔═══════════╗ ┃ ┃ ▲ ┃
┃ ║private key║──────decrypts─────────────┘ ┃
┃ ╚═══════════╝ ┃ ┃ ┃
┗━━━━━━━━━━━━━━━┛ ┗━━━━━━━━━━━━━━┛
Each PVYvault user owns a private vault to which only they have access. In addition to this, Shared Vaults can be used to share sensitive data between multiple members within an Organization. For more details on this, see the Organizations And Shared Vaults section.
¶ Organizations And Shared Vaults
Shared Vaults can be used to securely share sensitive data between multiple users. These vaults are provisioned and managed as part of Organizations, which deal with permission management as well as public key and identity verification.
¶ Vault Access Management
The previous sections describe how Vault data can be shared securely between multiple known accounts. An additional challenge lies in deciding who shall have access to a given vault as well as obtaining and verifying each accessors public key before encryption.
The organization structure depicted below determines which member shall have access to a given vault. Members can either be assigned to a Vault directly or indirectly via a Group.
┌──────────────┐ ┌──────────────┐ ┌──────────────┐
│ │ ╱│ │╲ │ │
│ Account │┼─────────○─│ Membership │──┼────────┼│ Organization │
│ │ ╲│ │╱ │ │
└──────────────┘ └───┬──────┬───┘ └──────────────┘
╲│╱ ╲│╱ ┼
○ ○ ○
│ │ ╱│╲
│ │ ┌──────────────┐
│ │ ╱│ │
│ └──────────────○─│ Group │
│ ╲│ │
○ └──────────────┘
╱│╲ ╲│╱
┌──────────────┐ ○
│ │╲ │
│ Shared Vault │─○──────────────────────┘
│ │╱
└──────────────┘
Every time a Vault participant encrypts the vault data, they perform the following steps:
- Determine accessors based on organization structure.
- Verify each accessor’s identity and public key (see
Verifying Members) - Encrypt the data using the steps outlined in
Shared-Key Encryption
Each participating member can now access the Vault data using their own private key.
¶ Metadata And Cryptographic Keys
In addition to Group and Member data, Organizations also hold the following information:
- The organization id is a random, unique identier assigned to it by the
server - The organization name is chosen by the organization owner and is mainly
used for display purposes - A RSA public key and private key pair that is used to sign and
verify public keys and identifying information of its members. See
Signing Member Information and
Verifying Members for details. - An AES key (in the following called “invites key”) used to encrypt the
invite verification code during
key exchange
The organization’s private key and invites key are considered secret and need therefore be encrypted at rest. For this, the organization acts as a Shared Crypto Container with the organization owners acting as accessors.
┏━━━━━━━━━━━━━━━┓ ┏━━━━━━━━━━━━━━━━━━━━┓
┃ Organization ┃ ┃ Organization ┃
┃ Owner ┃ ┃ ┃
┃ ┃ ┃ ╔═══════════════╗ ┃
┃ ┌ ─ ─ ─ ─ ─ ┐ ┃ ┃ ║┌─────────────┐║ ┃
┃ public key ──────encrypts──────▶║│ private key │║ ┃
┃ └ ─ ─ ─ ─ ─ ┘ ┃ ┃ ║└─────────────┘║ ┃
┃ ╔═══════════╗ ┃ ┃ ║┌─────────────┐║ ┃
┃ ║private key║──────decrypts──────▶║│ invites key │║ ┃
┃ ╚═══════════╝ ┃ ┃ ║└─────────────┘║ ┃
┗━━━━━━━━━━━━━━━┛ ┃ ╚═══════════════╝ ┃
┗━━━━━━━━━━━━━━━━━━━━┛
¶ Public Key Exchange And Verification
As with all cryptographic schemes that involve public-key encryption, a major challenge when dealing with shared vaults is securely exchanging and verifying the public keys and associated identities of all involved parties. This undertaking is complicated further by the fact that, although all communication and data transfer is generally mediated by a central server, PVYvault’s Zero-Trust Principle requires that this server (or any party potentially listening in on the connection) is never in the position to directly access any sensitive data or trick a participant into granting them access either directly or indirectly.
Instead of exchanging keys between all organization members directly, PVYvault uses a simple verification chain where the public keys and identfying information of all members are signed and verified with a dedicated RSA key pair owned by the organization (see Metadata and Cryptographic Keys). The
corresponding public key must in turn be signed and verified by each member using their individual, dedicated HMAC key.
¶ Trustless Server-Mediated Key Exchange
Before a new member can be added to an Organization, a key exchange has to take place between the organization (represented by the organization owner) and the new member. The key exchange is performed as follows:
- The organization owner
Ochooses a random passphrasep, a
random saltsand an iteration countias well as a random,
unique exchange id. p,sandiare used to generate the HMAC key
x = PBKDF2(p, s, i).Osigns the organizations public keypub_owithx:
sig_o = HMAC(x, pub_o)Osendss,i,pub_oandsig_oto the server
S, along with the exchange id and the recipients email address.- The server stores the received values and sends the invitation link (which
includes the exchange id) toIvia email. Iuses the exchange id to requests,i,pub_oand
sig_ofromS.IrequestspfromOvia a separate (and optimally secure)
channel of their choice. This can be in person, via phone or any by other
means.Igeneratesx = PBKDF2(p, s, i)using the obtained information.Iverifiespub_ousingxandsig_o.- Upon successful verification,
Isigns their own public keypub_i
usingx:sig_i = HMAC(x, pub_i) Isendspub_iandsig_itoS, which forwards them to
O.Overifiespub_iusingsig_iandx.
┌─────────────┐ ┌──────────┐ ┌───────────┐
│Org Owner (O)│ │Server (S)│ │Invitee (I)│
└──────┬──────┘ └────┬─────┘ └─────┬─────┘
┌─────────────────────┐ │ │ │
│p = [passphrase] │ │ s, i, id, email, │ │
│s = [random salt] │ │ pub_o, sig_o │ id (via email) │
│i = [iteration count]│ │─────────────────▶│─────────────────▷│
│x = PBKDF2(p,s,i) │ │ │ │
│pub_o = [public key] │ │ │ id │
│sig_o = HMAC(x,pub_o)│ │ │◀─────────────────│
│id = [invite id] │ │ │ s, i, │
│email = [inv. email] │ │ │ pub_o, sig_o │
└─────────────────────┘ │ │─ ─ ─ ─ ─ ─ ─ ─ ─▶│
│ │ │
│ │ p (in person) │ ┌─────────────────────┐
│────────────────────────────────────▷│ │pub_i = [public key] │
│ │ │ │x = PBKDF2(p,s,i) │
┌─────────────────┐ │ pub_i, sig_i │ pub_i, sig_i │ │x => verify sig_o │
│x => verify sig_i│ │◀─────────────────│◀─────────────────│ │sig_i = HMAC(x,pub_i)│
└─────────────────┘ │ │ │ └─────────────────────┘
│ │ │
│ │ │
│ │ │
▼ ▼ ▼
¶ Notes:
-
In practice, the member’s account id and email and the organization id are included in the respective signatures to protect these from tempering as well.
-
Since
pneeds to be sufficiently short to be conveniently entered by hand, it can potentially be guessed by eavesdroppers which would allow them to successfully perform a man-in-the-middle attack by injecting their own
public key. This is mitigated by using a sufficiently large iteration countiand invalidating key exchanges after a certain amount of time. -
Using a separate, direct communication channel for communicating the secret passphrase not only mitigates the risk of man-in-the-middle attacks but also means that the server
Sdoes not need to be explicitly trusted.
Furthermore, the risk of phishing attacks by a third party (including a malicious server admin) is greatly reduced since a direct, personal interaction between the parties is required. -
Since some time may pass between steps 1. and 7.,
pneeds to be stored securely for later reference. This is done by encrypting it with a dedicated AES “invites key” which is only accessible to organization owners. (See Metadata and Cryptographic Keys.
¶ Adding Members
Once the new member and organization have successfully exchanged public keys, these need to be stored in a way that allows both parties to be verify them later. The invitees public key (along with their identifying information) is signed by the organizations private key (only available to the organization owner) while the organizations public key is signed by the invitees own,dedicated HMAC key.
┏━━━━━━━━━━━━━━┓
┃Member Account┃
┃ ┃ ┌────────┐
┃╔════════════╗┃ │ sign │
┃║signing key ║──────────▶│ (HMAC) │◀────┐
┃╚════════════╝┃ └────────┘ │
┃┌ ─ ─ ─ ─ ─ ─ ┃ │ │
┃ public key │─────────────┐ │ │
┃└ ─ ─ ─ ─ ─ ─ ┃ │ │ │
┗━━━━━━━━━━━━━━┛ │ │ │
│ │ │ ┏━━━━━━━━━━━━━━┓
┏━━━━━━━━━━━━━━┓ │ │ │ ┃ Organization ┃
┃ Membership ┃ │ │ │ ┃ ┃
┃ ┃ │ │ │ ┃┌ ─ ─ ─ ─ ─ ─ ┃
┃┌ ─ ─ ─ ─ ─ ─ ┃ │ │ └───── public key │┃
┃ organization│┃ │ │ ┃└ ─ ─ ─ ─ ─ ─ ┃
┃│ signature ◀────────────│──┘ ┃╔════════════╗┃
┃ ─ ─ ─ ─ ─ ─ ┘┃ ▼ ┌─────║private key ║┃
┃┌ ─ ─ ─ ─ ─ ─ ┃ ┌────────┐ │ ┃╚════════════╝┃
┃ member │┃ │ sign │ │ ┗━━━━━━━━━━━━━━┛
┃│ signature ◀──────────│ (RSA) │◀────┘
┃ ─ ─ ─ ─ ─ ─ ┘┃ └────────┘
┗━━━━━━━━━━━━━━┛
¶ Verifying Members
Using the signatures described in the previous section, an organization member can verify the public key of any other member as follows.
- Verify the organizations public key using the organization signature created with their own HMAC key
- Verify the other member’s public key using the organization’s public key.
┏━━━━━━━━━━━━━━┓ ┏━━━━━━━━━━━━━━┓ ┏━━━━━━━━━━━━━━┓
┃ Account A ┃ ┃ Org ┃ ┃ Account B ┃
┃ ┃ ┌────────┐ ┃ ┃ ┌────────┐ ┃ ┃
┃╔════════════╗┃ │ verify │ ┃┌ ─ ─ ─ ─ ─ ─ ┃ │ verify │ ┃┌ ─ ─ ─ ─ ─ ─ ┃
┃║signing key ║────▶│ (HMAC) │◀──── public key │────▶│ (RSA) │◀─── public key │┃
┃╚════════════╝┃ └────────┘ ┃└ ─ ─ ─ ─ ─ ─ ┃ └────────┘ ┃└ ─ ─ ─ ─ ─ ─ ┃
┗━━━━━━━━━━━━━━┛ ▲ ┃╔════════════╗┃ ▲ ┗━━━━━━━━━━━━━━┛
│ ┃║private key ║┃ │ ┏━━━━━━━━━━━━━━┓
┏━━━━━━━━━━━━━━┓ │ ┃╚════════════╝┃ │ ┃ Membership B ┃
┃ Membership A ┃ │ ┗━━━━━━━━━━━━━━┛ │ ┃ ┃
┃ ┃ │ │ ┃┌ ─ ─ ─ ─ ─ ─ ┃
┃┌ ─ ─ ─ ─ ─ ─ ┃ │ │ ┃ member │┃
┃ organization│┃ │ └────────│ signature ┃
┃│ signature ┣─────────┘ ┃ ─ ─ ─ ─ ─ ─ ┘┃
┃ ─ ─ ─ ─ ─ ─ ┘┃ ┗━━━━━━━━━━━━━━┛
┗━━━━━━━━━━━━━━┛
¶ Organization Roles and Privileges
There are three distinct organization roles: Owner, Admin and basic Member. Each role comes with a different set of privileges. Some privileges are enforced cryptographically while others are enforced solely by the server.
¶ Basic Member
A basic organization member has the following privileges.
- Read the public data of other members, including id, email, public key and assigned vaults and groups.
- Read vault data of assigned vaults.
- Update vault data of assigned vaults where write permissions have been granted explicitly.
All of these privileges are enforced by the server (e.g. a vaults encrypted data will only be provided to a member if they are assigned to that vault) while access to the plain text data stored in vaults is also restricted cryptographically through the encryption mechanism described in Vaults.
¶ Admin
In addition to the privileges granted to basic members, admins also have the following privileges:
- Create and delete Vaults
- Assign vault access to groups and members directly
- Create, delete and manage groups
¶ Owner
In addition to the privileges granted to basic members and admins, organization owners also have the following privileges:
- Add/remove organization members
- Update a members id, email, public key or role
- Update the organizations public/private key pair
As described in a previous section, adding a new member to the organization requires access to the organizations private key. As described in Metadata and Cryptographic Keys, this access is restricted cryptographically to organization owners.
¶ Authentication And Data Transfer
Even though all sensitive information in PVYvault is end-to-end encrypted and theoretically secure even in case of an insecure connection or even a compromised server, PVYvault still uses a robust authentication scheme to limit access to user data, ensure payload integrity and enforce user permissions. A variation of the
Secure Remote Password protocol is used to authenticate users and establish a secure connection between client and server without exposing the user’s master password.
¶ User Signup
Whenever a user creates a PVYvault account, the following steps take place:
- Let
uandpbe the user’s email address and master
password, respectively. - The client
Csendsuto the serverS. - The server sends an email verification code
cto the user’s email
address. Cchooses a random saltsand iteration countiCgeneratesx = PBKDF2(p, s, i)and the password verifier
v = v(x)*Csendsu,v,s,iandctoSSverifiescand, if successful, storesu,v,s
andifor later use.
The signup process is now complete and the stored values can be used to verify the users identity and to negotiate a common session key.
┌──────────┐ ┌──────────┐
│Client (C)│ │Server (S)│
└─────┬────┘ └────┬─────┘
┌───────────────────┐ │ │
│u = [email address]│ │ u │
└───────────────────┘ │──────────────▶│ ┌───────────────────────┐
│ │ │c = [verification code]│
│ │ └───────────────────────┘
┌─────────────────────┐ │ c (via email) │
│p = [master password]│ │◁ ─ ─ ─ ─ ─ ─ ─│
│s = [random salt] │ │ │
│i = [iteration count]│ │ │
│x = PBKDF2(p,s,i) │ │ u, v, s, i, c │ ┌───────────────────┐
│v = v(x)* │ │──────────────▶│ │=> verify c │
└─────────────────────┘ │ │ │=> store u, v, s, i│
│ │ └───────────────────┘
│ │
▼ ▼
¶ Session Negotiation
In order to “log into” an existing account, a common session key needs to be negotiated. This happens as follows:
- Let
uandpbe the users email address and master password, respectively. - The client
Cgenerates the random valuesaandA* CsendsuandAto the ServerS.Slooks upsandibased onuand generates the random valuesbandB*.Ssendss,iandBtoC.Cgeneratesx = PBKDF2(p, s, i),K = K_client(x, a, B)andM = M(A, B, K)*.CsendsMtoS.Sgenerates its ownK' = K_server(v, b, A)andM' = M(A, B, K')*.Sverifies thatM == M'and thereforeK == K'. If verification fails, the session negotiation is aborted.- If successful,
SstoresKunder the session idsid. SsendssidtoC, which also stores it along withKfor later use.
Client and server now have a common and secret session key K which can be used for authenticating subsequent requests.
┌──────────┐ ┌──────────┐
│Client (C)│ │Server (S)│
└─────┬────┘ └────┬─────┘
┌───────────────────┐ │ │
│u = [email address]│ │ u, A │
│a, A = [random*] │ │──────────────▶│
└───────────────────┘ │ │ ┌────────────────┐
│ │ │b, B = [random*]│
┌───────────────────────┐ │ s, i, B │ └────────────────┘
│p = [master password] │ │◁ ─ ─ ─ ─ ─ ─ ─│
│x = PBKDF2(p,s,i) │ │ │
│K = K_client(x, a, B)* │ │ │
│M = M(A, B, K)* │ │ M │ ┌───────────────────────┐
└───────────────────────┘ │──────────────▶│ │K' = K_server(v, b, A)*│
│ │ │M' = M(A, B, K') │
│ │ │=> verify M == M' │
┌───────────────┐ │ sid │ │S = [session id] │
│=> store sid, K│ │◀ ─ ─ ─ ─ ─ ─ ─│ │=> store sid, K │
└───────────────┘ │ │ └───────────────────────┘
│ │
▼ ▼
¶ Request Authentication
Using the common session key K Client and Server can now authenticate each request as follows:
- Let
sidandKbe the previously negotiated session id and key. - Let
reqbe the intended request body andt1the time stamp at the time of the request. Cgenerates the signaturesig1 = HMAC(K, sid|t1|req).Csendsreq,sid,t1andsig1toS.Sverifiesreq,sidandt1usingsig1. If verification fails, or ift1is older than a predetermined maximum request age, the request is rejected.- Let
resbe the response body andt2the time stamp at the time of the response. Sgeneratessig2 = HMAC(K, sid|t2|res).Ssendsres,t2andsig2toC.Cverifiesres,sidandt2usingsig2. If verification fails, or ift2is older than a predetermined maximum response age, the response is rejected.
┌──────────┐ ┌──────────┐
│Client (C)│ │Server (S)│
└─────┬────┘ └────┬─────┘
┌──────────────────────────┐ │ │
│req = [request body] │ │ req, sid, │
│t1 = [timestamp] │ │ t1, sig1 │ ┌──────────────────────────┐
│sig1 = HMAC(K, sid|t1|req)│ │──────────────▶│ │=> verify sig1 │
└──────────────────────────┘ │ │ │res = [response body] │
│ │ │t2 = [timestamp] │
┌──────────────┐ │ res, t2, sig2 │ │sig2 = HMAC(K, sid|t2|res)│
│=> verify sig2│ │◁ ─ ─ ─ ─ ─ ─ ─│ └──────────────────────────┘
└──────────────┘ │ │
│ │
▼ ▼
* For details on how v, a, A, b, B, K
and M are generated, refer to
the SRP specification
¶ Notes
- Even though
vis based onp, it can not be used to guess the password in case someone eavesdrops on the connection or if the server is compromised. See section 4 of the SRP specification for details. - The session key
Kcannot be sniffed out since it is never transmitted. It could theoretically be guessed from the request signature but with a key size of 256 bits this is not really feasible either. - The salt and iteration count used for generating
xas well as the resulting authentication key are completely independent of the corresponding values used for encrypting the accounts private key, even though the derivation scheme and base passphrase are the same. - Request authentication works both ways. Not only can the server verify the users identity and knowledge of their master password, the client can also verify the identity of the server.
- The described authentication mechanism not only allows for identity verification, but also prevents tempering with the request/response body or timestamp.
- Rejecting request and responses older than a certain age mitigates the risk of replay attacks.
¶ Possible Attack Vectors and Mitigations
This section covers various possible attack vectors and mitigation steps taken.
¶ Man-In-The-Middle Attacks
A man-in-the-middle attack is an attack where the attacker secretly relays the communication between two parties in order to eavesdrop on the connection and/or temper with messages in transit.
MITM attacks may be launched in a multitude of ways, and even with technlogies like TLS, it is very hard to completely rule out that other parties may be listening in on the connection or even trying to tamper with the messages exchanged. Therefore, steps should be taken not only to mitigate the risk of a successful MITM attack, but also to ensure that even in case of an insecure connection, an attacker may never get access to any sensitive information or compromise the security of the application in any other way.
- Communication between the PVYvault client and server is always secured through
Transport Layer Security. - No sensitive information is ever transmitted in plain text.
- Transmitted data is protected from tampering through PVYvault’s strong
Authentication Mechanism. - PVYvault’s Key Exchange Mechanism
is designed to be secure even over an untrusted connection.
¶ Phishing
With the addition of Organizations And Shared Vaults in PVYvault 3, phishing has become a potential attack vector as well. Attackers may try to lure PVYvault users into sharing sensitive information by inviting them to misleadingly named organizations which can be mistaken for an employer or friend. Users could then accidentally share data within vaults assigned to them.
However, the procedure for inviting and adding a new member to an organization is designed in a way that makes this very hard to accomplish, since it requires direct, personal coordination between both parties. See Trustless Server-Mediated Key Exchange for more details.
¶ Guessing Master Passwords
PVYvault uses a combination of various strong encryption algorithms to
protect all sensitive data and cryptographic keys both at rest and during transmission. The master password acts as a universal key for this encryption scheme.
Master passwords are never stored anywhere and should only ever be known by the PVYvault user themself. Unfortunately, since this means that in the majority of use cases the user will have to commit this password to memory, the “key space” of feasible passwords is relatively limited. Additionally, since master passwords are ultimately chosen by the user, no guarantee can be made to the strength or randomness of these passwords. We strongly advise PVY-ID Organisation Admin’s to use at least 22 randomized Character as their PVY-ID Login Passwords.
This means that master password are a prime-target for guessing attacks of all sorts and steps should be taken to make these attacks either infeasible or, at a very minimum, too costly to be worthwhile. This we addresss within our Deployment and Security Methods.
¶ User Enumeration
With the use of PVY-ID by E-Mail Address, Password, additional MFA such as OTP or Biometric Authentication, even a correctly guessed Username can not succeed to login, since it would require a brutforce attack on password guessing, and would stop latest on MFA.
Our Systems are designed to block immediately a wrong entered PVY-ID authentication after 2 attempts blocking the IP Source for 30 Minutes. Our intelligent protection systems can differentiate if a real user is entering a password, or if its bot driven automation. Learn more about on Authentication and Firewall - WAF Section below.
¶ Password Spraying
Password spraying, an attack similar to brutforce, just opposite around, going with a single password againts multiple guessed possible usernames in an automated manner is eliminated on several Levels
¶ Service Level
With the use of our state of the Art Cybersecurity Solutions in Place, both malicious IPs and Subnets are being blocked by default within an update intervall of 15 seconds, using both cybersecurity community-driven and commercial driven sources. Enhanced Security mechanism blocking the source of IPs if malicious login attempts taken effect.
¶ Authentication Level
While we use as authentication SSO mechanism, with its additional security measurements, authenticiation directly to the PVYvault System is disabled. Any attack has to be placed against the PVY-ID SSO System, which protected with various measurements.
¶ Firewall - WAF & Realtime Access Log with ML/AI
Beside of our Multi-Level Firewalling Concept, we also have for each critical Service so called Wep App Firewalls as an additional Protection Layer in Charge, like Crowdsec and Wazuh. Abnormal Behaviour is autonomously dedected from the Protection System itself, even attempts againts JS CVE queries.
¶ Denial Of Service
Beside the our default Security Measurements on the Deployments, we run not only Multi-Level Firewalls with IPS and DDoS Protection for each of the Customer Deployments, but also Firewalling on hardened deployment nodes on top. A Carrier and MAN DDoS Protection into the Backbones ensures, that even if a large scale DDoS Attacks is being iniated, that the packets of such attacks are discarded before it even reach the BGP of our Datacenter Entry Points.
¶ Compromised Server
To Prevent a comprimised Server, we took several security measurements, which even got suprisingly acknownledged by one of the oldest Cybersecurity Experts in Europe, Mr. Eric Filiol. For Datacenter driven deployments, only 5 People having access to our Infrastructure, which we own til the last screw. On Deployment Level, we made several security measurements not seen elsewhere in the SaaS or PIAAS Industry, to ensure a Server can’t be compromised. Furthermore, our orchestrated services running virtualized either as KVM or ContainerD over the Virtualisation Cluster, where we run either Kubernetes Clusters on top of it, hardened, and the customer applications is furtermore deployed in a own hermetic sealed environment using non-privileged Pods or Dockers. We ensure with limited personal, background checked and personally known for over 15 years, that only a handful people having access to our Infrastructure.
Additional Principals and Tools in Place, such as Netbox, Wazuh, Crowdsec, Autin and constantly rotating encrypted deployment credentials, with real time audit and logs, prevent malicious interaction without further notices. Each Access logs and its performed commands and queries over ssh, bash or inspect, are being logged and stored in multiple independent systems.
¶ Software Code Integrity and CVE Checks.
Before even an App or Server is being compiled, built and packed as Docker Image or Pod, it runs over our own GitLab Pipeline Checks over various Integrity and CVE Checks. And yes, we have dedicated team just checking this accordingly on every build before we stage and iteration to testing or production environments. We have intensive internal guide lines and each of our DevPops and Lead Developer is using Company owned Devices which are constantly monitored and Code Integrity Checks already takes place on the Development Environements, using Podman Desktop with Realtime Security Plugins which checks against CVEs, Stack related Querries and Inspection of the final local built Container, before GitLab does the same on the production build process again.
¶ Cryptographic Algorithms And Configurations
¶ Symmetric Encryption
For all symmetric encryption operations, the
AES Cipher is used in GCM mode with a key size of 256 bits.
Areas of use:
¶ Asymmetric Encryption
For asymmetric encryption operations, the RSA-OAEP algorithm is used with a modulus length of 2048 bits and the
SHA-256 hash function.
Areas of use:
¶ Symmetric Signature Schemes
For symmetric signature creation and verification, the HMAC algorithm is used with a key length of 256 bits and the SHA-256 hash function.
Areas of use:
¶ Asymmetric Signature Schems
For asymmetric signature creation and verification, the RSA-PSS algorithm is used with a modulus length of 2048 bits, a salt length
of 256 bits and the SHA-256 hash function.
Areas of use:
¶ Password-Based Key Derivation
For password-based key derivation, the PBKDF2 algorithm is used with the SHA-256 hash function and a salt length of 128 bits. The iteration count varies by area of use.
Areas of use:
¶ Additional WAF/WAP on each Deployment
Each PVY@Cloud Customer benefits on Top of PVYvpn and PVYsecurity over its core firewalls, Crowdsec IPS Protection with DDoS Protections for all deployed Application. So it is save, even you don’t use PVYvpn as the last hardening option.
Yes, we have an API available. However, since we use PVY-ID as Authentication over the Webauthn SSO Protocol, the Purpose for the API will be limited to other PVYapps only, such as PVYautomator, PVYterminal, PVYdeployer with CORS and CPS masterdomain specific restrictions for each customer. The Documentation for it will be published once here, soon we have ready some nice use cases for you.
The App automatically takes the Default Language of your Operating System. Currently supported languages are:
- English
- German
- Spanish
- Italian
- French
If you use a different language and you understand english or french, make sure, that in the regional Settings in your OS you ad english as second Language, not as primary. After this is made and taken on OS Level in Effect (Windows requires reboot, macOS takes it instantly and Linux requires User log-off and login) your secondary language is being taken from PVYvault as Display Language. We are working on more internationalization and adding new languages on each new release.
To make it easier for you, we have created a couple of “How-to” Videos how to setup and configure a Yubi Key for Hardware Key based Authentification on Top of your PVY-ID (It can be activated for PVY-ID itself as well in PVYcentral) and each a Video how to enable Biometric Authentication for macOS and Windows Users on PVYmedia:
{{Video-Playlist-Link}}
Many People are not aware about the traces they leave on the Internet in their daily habbits and that this traces can turn against you, in several aspects, such as Pishing Attacks, Hacking attempts, Malware attempts among the Data-brokering with your traces.
¶ For Example:
A Macbook Pro 16", with closed Lid, in active, no App active, send per Hour around 180MB of Data back to Apple Geolocation Ingress, which includes Data of your Network, WLAN Name even you deactivated Geo-Location Systemwide, except: Find my Device. It comes even worse, when activate the so called “Privacy Settings” in Apple Mail and Safari to mask your IP.
If you installed Youtube as App on a iOS Device, and logged-in with your Google/Youtube Account, you would go crazy to see how much data from you are being collected from your device.
¶ Stay focused and orgnized
There are many ways out there, how to avoid to much traces in the net. But we will focus here on some simple measurements, anyone can follow with just a little efforts in a logic way. And how to reflect this with PVYapps such as PVYvault, PVYlocal and PVYnews. And this applies as a Private Internet User as well as an Employee in any Organization.
First of all, we break down the Usuage of Online Identies you need today to manage your Business with Procurrement / Suppliers, Onlineshops, Sales Activities, Marketing, dealing with Authorities such as GoV or Tax Offices and so one. We call this in our example “Sections”.
¶ As Organization / Business
As an Sys Admin of your Organizaton, which you have to manage, you probably end up with a following Minimum Section Structure:
- Social Media
- Marketing
- Logistics
- Procurrement
- Travel
- GoV & Authorities
- Tax & VAT
- Banking
- Insurances
- Sales
- Pre-sales
- Support / HelpDesk
For each of them, you not only create a dedicated Organization Vault, (you may want to split that up into Regions or Teams) but you also create on PVYgroupware, respectively on PVYcentral “Shared Inboxes” as Organization official E-Mail Address, which you then bind to these specific Vaults.
Your employee shall create, if they have dedicated accounts for Social Media for example, an Non-personified E-Mail Alias in their PVYgroupware Web Access. Please be aware, that Data-brokering also is a big factor in the business world and it is criminally neglected, especially if using the GAFAM Providers such as Google, Apple, Facebook/Meta, Amazon and Salesforce to name the big ones only.
For sure, a great firewall with blocklist for ads, dns domain and ip filter is mandatory. Only allow, what is really needed, so each team can thrive accordingly.
For your Website you may want to try PVYcaptcha, a non invasive tracking-less free Captcha Service. It will not affect your Search Ranking on the Major Players, but can help to lower your adword costs significantly, since Google not only tracks the visitors with their ReCaptcha/Google Captcha Spam Protection, but also measures how your Website performs on Forms / Shopping Cart Fields for Checkout.
¶ As private User / Family
As an Family Guy or Private Person, your Core Section for your online habbits looks similar, a bit different, but mostly like:
- Social Media
- Online Shopping
- Gaming
- Dating/Clubs
- Shopping for Work
- Travel
- Pets
- Car
- Sport
- Education/School
- GoV & Authorities
- Tax & VAT
- Banking
- Insurances
For each of this Section you create your own Personal Vault. Or if certain Login Credentials to local major suppliers like Home Delivery of your favorite groccery are being shared with family members, you create an Organisation and call it “My Family” and adding the specific Vaults on PVYvault there, create some groups such as:
- All
- Parents
- Kids
and allocate these Groups to the Vaults accordingly and adding the members there. When done, you create on several Mail Service Provider for each of this section an non-personified e-mail account. We recommend to use their Webmail in Browser, but you can add them for more conviniences also to some of your Mail Clients.
This way you segregate the data traces in the Web for your daily habbits at least for the data brokers, if you take care of some little nice tools to use.
A privacy focused Web Browser such as
- Orion Web Browser (highly recommended)
- Duck Duck Go Browser
¶ Using AdGuard
Considering to use Adguard as your local DNS Server, with Upstream to your Modem. If you are skilled in IT, buy a MiniPC or RasberryPie, configure it with .2 as IP accordingly to your DHCP Client Network, choose your modem as upstream or 9.9.9.9 as Upstream DNS. Set on the DHCP Settings in the Router/Modem from your ISP as DNS this Adguard IP, so it will be automatically propagated to all your Devices in your Net and all users benefit by ad blocking, malware and phishing protection. There is also Parental Control included, you can exlude relative easy some devices for it as Admin. Please Note, Adguard is fare above Pi-Hole and they have a constantly development pace. You can also buy devices with adguard on it. Its fare better than any “Browser Extension”.
Use PVYsearch instead of Google or Bing, it delivers you a better accurarcy and more option to fine tune search, where your Search Queries are not bonded to an User-ID and not harvested, secondly, its Ad and Tracking Free, and Orion Web Browser takes them out, without the ugly warning, you may have an Ad Blocker Extension (Remove that) in use.
¶ Avoid:
- Google Services
- Facebook Meta Apps such as Facebook, Instagram, Whatsapp
- Apple Geolocaton Services
- Apple Privacy Options such as Mask my IP
- Google or Apple iCloud Sync for Photos/Documents/Passwords!
- OpenAI, ChatGPT, use Deepseek or Local AI such as PVYai or deploy with Ollama your own local stack
Please not: Alone Facebook and Google making at least 700 USD per year with data brokering of your traces. With Organization traces more then factor 20.
¶ Availablity
PVYvault is for each PVY-ID Customer / User, regardless of the chosen deployment option, as an Default App included, to give our Customer a great solution to become owner and master of their own Passwords.
| PVY Deployment Type | Subscription Level | Exposed by default | PVYvpn optional |
|---|---|---|---|
| PVY@Cloud | PVY@me | Websecure SSL (443) | Yes, from Appstore |
| PVY@Cloud | PVY@premium | Websecure SSL (443) | Yes, from Appstore |
| PVY@Cloud | PVY@business | Only via PVYvpn | - |
| PVY@Cloud | PVY@business | Only via PVYvpn | - |
| PVY@Cloud | PVY@enterprise | Only via PVYvpn | - |
| PVY@Home Appliance | PVY@Home | Only via PVYvpn | - |
| PVY@Office Appliance | PVY@Office | Only via PVYvpn | - |
If you use also PVYbackup as an optional available Application Service for PVY@Cloud Users, (included on PVY@Home and PVY@office Appliances), follow the guides we published in PVYbackup Documentation, to benefit from automatic Snapshoting of the PVYvault Database, File Storage as an encrypted Restic based Backup with 1-Click Restore Options.
We can not restore accidently deleted Vaults or Users on PVYvault running on us. If you run it dedicated on your PVY@Home Appliance, PVY@Office Appliance or PVY@business/PVY@enterprise, You will likely have an encrypted Backup using PVYbackup, so you can roll back.